woofV post-process populated rootfs
Previous post in woofV project:
https://bkhome.org/news/202402/woofv-populated-rootfs.html
...the script '5populate-rootfs' populated folder 'rootfs' with
all the packages.
Now, '6post-process-rootfs' has been implemented. This makes lots of modifications to 'rootfs'. The script is here:
https://github.com/bkauler/woofq/tree/main/easyos/easy-code/rootfs-skeleton/usr/local/woofV/rootfs
...a lot of code in '6post-process-rootfs', mostly ported from '2createpackages' and '3buildeasydistro' scripts in WoofQ, so I didn't write all of that from scratch.
Next-up, create 'easy.sfs' and then the drive-image; I wonder if
will get a desktop?!
Tags: easy
woofV populated rootfs
Here is the previous post in the woofV project:
https://bkhome.org/news/202402/woofv-populate-rootfs.html
There has been bug-fixing, and now the '5populate-rootfs' script populates the 'rootfs' folder with all packages, with only a few minor errors. This 'rootfs' will become 'easy.sfs' and hence a new release of easyVoid.
The package selection is similar to that in easyVoid 6.0.2 that was released for early pre-alpha testing, see the forum:
https://forum.puppylinux.com/viewtopic.php?t=9553
...that easyVoid uses PKGget (PPM), not the XBPS package manager.
The big difference now, is have populated 'rootfs' using XBPS. The intention is that PKGget will become a GUI frontend for XBPS -- but that has not yet been implemented.
This 'rootfs' has 1064 packages; here they are:
915resolution-0.5.32012052164_1 Intel Video BIOS Hack
AppStream-0.16.4_1 Tools and libraries to work with AppStream metadata
CellWriter-1.3.6_2 Grid-entry natural handwriting input panel
CoinMP-1.8.4_1 Library that supports most of Coin CLP, CBC and CGL
Dropbox_GUI-0.3.11_1 Dropbox GUI 0.3.1
Global_IP_TV_Panel_Any_Pup_using_mpv-20237_1 Global IP TV Panel
NetworkManager-1.32.10_6 NetworkManager
OpenCL-Headers-2023.12.14_1 Khronos OpenCL (Open Computing Language) header files
Pup-SysInfo-3.5_1 System information utility
SDL-1.2.15_14 Simple Directmedia Layer
SDL2-2.28.5_3 Simple DirectMedia Layer (version 2)
SDL_gfx-2.0.26_2 Graphics drawing primitives for SDL
SDL_image-1.2.12_13 Load images as SDL surfaces
SDL_mixer-1.2.12_14 Multi-channel audio mixer library
SDL_sound-1.0.3_8 Library to decode several popular sound file formats
SDL_ttf-2.0.11_7 Use TrueType fonts in your SDL applications
UrxvtControl-1.31_1 Urxvt configuration
abseil-cpp-20230802.1_1 Abseil common libraries
acl-2.3.1_1 Access Control List filesystem support
adbfs-2018072081745_6 Mount Android phones on Linux with adb. No root required.
adwaita-icon-theme-44.0_1 Theme consisting of a set of icons for GTK+
align-1.7.5_1 align text into columns
alsa-lib-1.2.11_1 Advanced Linux Sound Architecture (ALSA) library
alsa-plugins-1.2.7.1_2 Advanced Linux Sound Architecture (ALSA) extra plugins
alsa-plugins-pulseaudio-1.2.7.1_2 Advanced Linux Sound Architecture (ALSA) extra plugins - Pulseaudio output plugin
alsa-utils-1.2.11_1 Advanced Linux Sound Architecture (ALSA) utilities
android-tools-5.1.1.37_6 no description
appres-1.0.6_1 List X application resource database
apr-1.7.0_4 Apache Portable Runtime Library
apr-util-1.6.3_4 Apache Portable Runtime Utility Library
argon2-20190702_3 Password hashing function
arp-scan-1.10.0_1 Tool that uses ARP to discover IP hosts on the local network
aspell-0.60.8_5 Spell checker with good multi-language support
at-spi2-atk-2.48.0_1 Assistive Technology Service Provider Interface - ATK bridge
at-spi2-core-2.48.0_1 Assistive Technology Service Provider Interface
atf-libs-0.21_4 Automated Testing Framework - runtime libraries
atk-2.48.0_1 Set of interfaces for accessibility
atkmm-2.28.3_1 Set of interfaces for accessibility (C++ bindings)
attr-2.5.2_1 Extended attribute support library for ACL support
audiofile-0.3.6_4 C library for reading and writing audio files
aufs-util-4.983559_6 Tools for managing AUFS mounts
avahi-glib-libs-0.8_7 Avahi glib shared libraries
avahi-libs-0.8_2 Avahi shared libraries
awf-1.4.0_6 A widget factory for gtk2 and gtk3
bacon-hug-0.109_6 High level GUI for BaCon
bash-5.2.21_1 GNU Bourne Again Shell
bbc-provided-2003_6 no description
bc-1.07.1_5 Arbitrary precision numeric processing language
bdftopcf-1.1_6 bdftopcf is a tool to convert BDF fonts to PCF fonts
bitmap-1.1.1_1 Bitmap editor and converter utilities for X
bluepup-tray-20160922_6 Tray applet used by BluePup in EasyOS and Quirky Linux
bluez-5.62_6 Linux Bluetooth Stack Userland V5
bluez-tools-2.020170911_6 Commandline tools for bluetooth
bones-0.3.1_1 simple project version control
brotli-1.1.0_1 Generic-purpose lossless compression algorithm
bubblewrap-0.8.0_1 Unprivileged sandboxing tool
busybox-1.36.164_1 linux utilities, compiled statically with musl
bzip2-1.0.8_2 Freely available, patent free, high-quality data compressor
c-ares-1.26.0_1 Library for asynchronous DNS requests
ca-certificates-20240203+3.98_1 Common CA certificates for SSL/TLS from Mozilla
cairo-1.18.0_1 Vector graphics library with cross-device output support
cairomm-1.14.5_1 C++ bindings to Cairo vector graphics library
cddetect-2.11_6 Detect CD inserted in drive.
cddetect-quick-20081_6 no description
cdparanoia-10.2_15 CDDA reading utility with extra data verification features
cdrtools-2023.09.28_3 Schily's portable tools - cdrtools
celluloid-0.26_1 Simple GTK+ frontend for mpv
celt-0.11.3_3 An audio codec for use in low-delay speech and audio communication
cgtkcalc-2.2.4_6 a simple scientific calculator for complex numbers
chromaprint-1.5.1_1 Library that extracts fingerprints from any audio source
chrome-skel-ask-20231215_1 Chrome web browser
chrpath-0.16_6 Tool to edit rpath in ELF binaries
cifs-utils-6.15_1 CIFS filesystem user-space tools
clucene-2.3.3.4_10 Text search engine written in C++
coreutils-9.4_1 GNU core utilities
cpio-2.15_1 GNU copy-in/out (cpio) with remote magnetic tape (rmt) support
cups-2.4.7_4 Common Unix Printing System
cups-filters-1.28.17_4 OpenPrinting CUPS Filters
cups_pdf-0.82_1 print to pdf file
curl-8.6.0_1 Client that groks URLs
curlftpfs-0.9.2_6 A filesystem for accessing FTP hosts based on FUSE and libcurl
cyrus-sasl-2.1.28_4 Cyrus SASL - auth daemon and administration tools
dbus-1.14.8_6 D-Bus message bus
dbus-glib-0.112_6 High level language GLib binding for D-Bus
dbus-libs-1.14.10_1 Message bus system - shared libraries
dbus-x11-1.14.10_1 Message bus system - X11 support
dconf-0.40.0_1 Low-level configuration system
defaults-chooser-0.9.21_1 Default Applications Chooser
dejavu-fonts-ttf-2.37_2 DejaVu family of TrueType fonts
desk_background_galah_pink_grey1-20240121_1 pale graduated grey with easyvoid text
desk_background_greyscale_easyvoid-20240117_1 pale graduated grey with easyvoid text
desk_background_pale-orange-brown-red-20230209_1 very pale orange brown red with easyos text
desk_icon_theme_treepata_black_pinkish-20240204_1 high contrast black icons
desk_icon_theme_very-light-orange-20230601_1 desktop icons, based on a minimal theme by jq8, with added stark grey and very-light-orange fill
desktop-file-utils-0.27_1 Utilities to manage desktop entries
device-mapper-2.03.23_1 Device Mapper userspace library and tools
dhcpcd-9.4.1_6 dhcpcd - a DHCP client
dia-0.97.3_4 GTK+ based diagram creation program
dialog-1.3.20240101_1 Tool to display dialog boxes from shell scripts
diffstat-1.66_1 Display a histogram of diff output
diffutils-3.10_1 GNU diff utilities
disktype-942_6 Disk type identification utility
djvulibre-3.5.28_2 Utilities for the DjVu image format
dmidecode-3.5_1 Desktop Management Interface table related utilities
dnsmasq-2.89_1 Lightweight, easy to configure DNS forwarder and DHCP server
dnssec-anchors-20230213_1 DNSSEC trust anchors for the root zone
dosfstools-4.2_1 DOS filesystem tools
double-conversion-3.3.0_1 Efficient binary-decimal and decimal-binary routines for IEEE doubles
dpkg-1.22.0_1 Debian Package Manager
droidcam-1.8.2_6 turn android and iphone into a webcam
duktape-2.7.0_1 Embeddable JavaScript engine
dvd-close-7.12014_6 Utility to close optical madia tray
dvdauthor-0.7.2_4 DVD authoring tools, generate a DVD movie from MPEG2 stream
e2fsprogs-1.47.0_2 Ext2/3/4 Filesystem Utilities
e2fsprogs-libs-1.47.0_2 Ext2/3/4 Filesystem Utilities - shared libraries
easycast-2.0_1 EasyCast screen recorder
editres-1.0.8_1 Dynamic resource editor for X Toolkit applications
efibootmgr-18_1 Tool to modify UEFI Firmware Boot Manager Variables
elfutils-0.190_1 Utilities to handle ELF object files
ell-0.50_1 Linux library for embedded development
elogind-252.9_2 Standalone logind fork
empty-0.6.20_6 run processes under pseudo-terminal sessions
enchant2-2.6.4_1 Generic spell checking library
eudev-3.2.14_1 Fork of systemd-udev (enhanced userland device daemon)
eudev-libudev-3.2.14_1 Fork of systemd-udev (enhanced userland device daemon) - runtime library
evince-44.3_1 GNOME Document viewer for multiple document formats
exfat-utils-1.4.0_1 Utilities for exFAT file system
exiv2-0.28.1_1 Image metadata manipulation
expat-2.6.0_1 XML parser library written in C
faac-1.30_1 AAC audio encoder library
fdk-aac-2.0.3_1 Fraunhofer FDK AAC codec library
ffconvert-1.4.21_1 FFConvert multimedia converter
ffmpeg-4.4.4_6 Decoding, encoding and streaming software
ffplay-4.4.4_6 Simple video player using FFmpeg and SDL2
fftag-2.11_1 audio and video file meta tagger
file-5.45_1 File type identification utility
findutils-4.9.0_1 GNU Find Utilities
firefox-122.0_1 Mozilla Firefox web browser
firefox-i18n-bg-122.0_1 Firefox Bulgarian language pack
firefox-i18n-cs-122.0_1 Firefox Czech language pack
firefox-i18n-da-122.0_1 Firefox Danish language pack
firefox-i18n-de-122.0_1 Firefox German language pack
firefox-i18n-el-122.0_1 Firefox Greek language pack
firefox-i18n-et-122.0_1 Firefox Estonian language pack
firefox-i18n-fi-122.0_1 Firefox Finnish language pack
firefox-i18n-fr-122.0_1 Firefox French language pack
firefox-i18n-hr-122.0_1 Firefox Croatian language pack
firefox-i18n-hu-122.0_1 Firefox Hungarian language pack
firefox-i18n-is-122.0_1 Firefox Icelandic language pack
firefox-i18n-it-122.0_1 Firefox Italian language pack
firefox-i18n-lt-122.0_1 Firefox Lithuanian language pack
firefox-i18n-lv-122.0_1 Firefox Latvian language pack
firefox-i18n-mk-122.0_1 Firefox Macedonian language pack
firefox-i18n-nb-NO-122.0_1 Firefox Norwegian (Bokmål) language pack
firefox-i18n-nl-122.0_1 Firefox Dutch language pack
firefox-i18n-nn-NO-122.0_1 Firefox Norwegian (Nynorsk) language pack
firefox-i18n-pl-122.0_1 Firefox Polish language pack
firefox-i18n-ro-122.0_1 Firefox Romanian language pack
firefox-i18n-ru-122.0_1 Firefox Russian language pack
firefox-i18n-sk-122.0_1 Firefox Slovak language pack
firefox-i18n-sl-122.0_1 Firefox Slovenian language pack
firefox-i18n-sq-122.0_1 Firefox Albanian language pack
firefox-i18n-sr-122.0_1 Firefox Serbian language pack
firefox-i18n-sv-SE-122.0_1 Firefox Swedish language pack
firefox-i18n-tr-122.0_1 Firefox Turkish language pack
firefox-i18n-uk-122.0_1 Firefox Ukrainian language pack
firefox-i18n-uz-122.0_1 Firefox Uzbek language pack
firmware_asus_e200ha-201603244.4.6_1 firmware for asus e200ha notebook. running 4.4.6 kernel
firmware_linux_acer_aspire1-5.220190813_1 firmware for acer aspire1
firmware_linux_all_k5p15p85-20230201_1 firmware for 5.15.85+ kernel
firmware_linux_base-4.13_1 kernel in-tree firmware that got taken out for 4.14+ kernels
firmware_linux_mele_pcg35-20170927_1 wifi firmware for mele pcg35 mini-pc
firmware_linux_rtw89-20230710_1 rtw89 kernel firmware
flac-1.4.3_1 Free Lossless Audio Codec
flatpak-1.15.6_1 Application sandboxing and distribution framework
flite-2.2_1 Lightweight speech synthesis engine
floppy-format-noarch-20190203_1 Format Floppy disks, internal and usb drives
flsynclient-0.63_6 GUI to manage Synaptics touchpad
fltk-1.3.8_1 Cross-platform C++ GUI toolkit
font-alias-1.0.5_1 Standard aliases for X11 PCF fonts
font-util-1.4.1_1 Tools for truncating and subseting of ISO10646-1 BDF fonts
font_opensans_semibold_bold-201312141_1 sans-serif, semi-bold and bold -- bold is very bold. using in quirky 6.0
fontconfig-2.14.2_1 Library for configuring and customizing font access
fonttosfnt-1.2.3_1 Wraps a set of bdf or pcf bitmap fonts in a sfnt OpenType wrapper
fpm2-0.90_6 An application that allows you to securely store your passwords.
freememapplet-tray-2.6_6 Tray applet for EasyOS show free storage
freetype-2.13.2_1 Font rendering engine and library API
fribidi-1.0.13_1 Free Implementation of the Unicode Bidirectional Algorithm
fuse-2.9.9_1 Filesystem in Userspace
fuse3-3.16.2_1 Filesystem in Userspace 3.x
galculator-2.1.4_3 GTK+ based scientific calculator (GTK+3)
gamin-0.1.10_2 Library providing the FAM File Alteration Monitor API
gawk-5.1.1_1 GNU awk utility
gc-8.2.6_1 Garbage collector for C and C++
gcolorsel-1.0.0_6 It is a program to select colors with a GTK 2.0 interface
gcr-3.41.1_1 GNOME crypto package
gd-2.3.3_2 Graphics library for the dynamic creation of images
gdbm-1.23_1 GNU database routines
gdk-pixbuf-2.42.10_2 Image loading library for The GTK+ toolkit (v2)
gdk-pixbuf-xlib-2.40.2_1 Image loading library for The GTK+ toolkit (v2)
gdmap-0.8.1_6 GdMap is a tool which allows to visualize disk space.
geany-1.38_1 Fast and lightweight IDE
gettext-0.21_4 Internationalized Message Handling Library and tools
gfnrename-0.618_6 gFnRename is a simple utility to rename multiple files.
gftp-2.0.19_9 Graphical file transfer client
ghostscript-10.02.1_1 Interpreter for the PostScript language
gif2lss-0.4_6 A utility for converting 16 color gif images to LSS encoding.
giflib-5.2.1_1 Library to handle, display and manipulate GIF images
gifsicle-1.88_6 A tool for creating gif animations.
gir-freedesktop-1.76.1_3 Introspection data for some FreeDesktop components
glew-2.2.0_1 OpenGL Extension Wrangler Library
glib-2.78.0_3 GNU library of C routines
glib-networking-2.76.0_1 Network-related giomodules for glib
glibc-2.38_5 GNU C library
glibc-locales-2.38_5 GNU C library - locale data files
glibmm-2.66.6_1 C++ bindings for GLib
glslang-11.11.0_1 Khronos reference front-end for GLSL, ESSL, and sample SPIR-V generator
glu-9.0.3_1 Mesa OpenGL utility library (GLU)
glxinfo-8.4.0_3 Tool to diagnose problems with 3D acceleration setup
gmeasures-0.718_6 A simple utility to convert weights and measures and temperature.
gmp-6.3.0_1 Library for arbitrary precision arithmetic
gnet-2.0.8_6 A network library
gnome-desktop-44.0_1 GNOME desktop management utilities
gnome-doc-utils-stub-1.0_6 Stub implementation of gnome-doc-utils
gnome-keyring-40.0_6 Password and keyring managing daemon
gnome-menus-2.14.3_6 GNOME menus
gnupg-2.4.3_2 GNU Privacy Guard (2.x)
gnutls-3.8.3_1 GNU Transport Layer Security library
gobject-introspection-1.76.1_3 Introspection system for GObject-based libraries
gparted-1.5.0_1 Gnome Partition Editor
gpgme-1.23.1_2 GnuPG Made Easy
gpgmepp-1.23.1_2 GnuPG Made Easy - C++ library
gpptp-2.118_6 Linux PPTP Client
gpptp-noarch-2.020220328_1 Gpptp v2.0 PPTP VPN client
gptfdisk-1.0.8_6 Utility for modifying GPT disk partitioning
graphene-1.10.8_1 Thin layer of types for graphic libraries
graphite-1.3.14_1 Reimplementation of the SIL Graphite text processing engine
grep-3.7_6 GNU grep utility
gsettings-desktop-schemas-44.0_1 Collection of GSettings schemas
gsl-2.7.1_1 Numerical library for C and C++ programmers
gspell-1.12.2_1 Flexible API to add spell checking to a GTK+ application
gst-plugins-bad1-1.22.9_1 GStreamer plugins from the bad set (v1.x)
gst-plugins-base1-1.22.9_1 GStreamer Base Plug-ins (v1.x)
gstreamer1-1.22.9_1 Core GStreamer libraries and elements (1.x)
gtk+-2.24.33_2 GTK+ toolkit (v2)
gtk+3-3.24.38_1 GTK+ toolkit (v3)
gtk-update-icon-cache-2.24.33_2 GTK+ toolkit (v2) - The GTK+ update icon cache tool
gtk4-4.12.3_1 GIMP ToolKit (v4)
gtk_2_3_theme_flat-grey-rounded2-20240117_1 Flat grey rounded theme for gtk2 and gtk3 created by dimkr
gtk_2_3_theme_flat-light-orange-brown-20230208_1 flat gtk2 and gtk3 theme, very light brown and orange
gtk_theme_citrus_cut-1.2_1 gtk2 orangy theme
gtk_theme_peachy_red-20170105_1 peachy-red gtk2 theme
gtkdialog-0.8.4514_6 A utility for creating X11 dialog boxes
gtkhash-1.2_6 gui to create hashes
gtkmm-3.24.8_1 C++ bindings for The GTK+ toolkit (v3)
gtkmm2-2.24.5_4 C++ bindings for The GTK+ toolkit (v2)
gtksourceview-3.24.11_1 Text widget that extends GTK+3 GtkTextView widget
gtksourceview2-2.10.5_8 Text widget that extends GTK+ GtkTextView widget
gtksourceview4-4.8.2_2 Text widget that extends GTK+ GtkTextView widget
guile-2.2.7_3 Portable, embeddable Scheme implementation written in C
gummiboot-20150311164_1 efi boot manager
gutenprint-5.3.4_1 Top quality printer drivers for POSIX systems
gview-0.9.1_6 A tiny simple gtk image viewer
gwaveedit-20220803_6 A graphical program for editing playing and recording sound files.
gwhere-20210113_6 Removable media catalog manager
gxlat-0.4_1 Gxlat language translator
gxmessage-3.4.3_2 Clone of xmessage based on GTK+
gzip-1.13_1 GNU compression utility (replacement for compress)
hardinfo-20150425_6 A system profiler and benchmark for Linux systems
harfbuzz-8.3.0_1 OpenType text shaping engine
helpsurfer-0.6_6 A tiny web browser for viewing local html files.
hiawatha-10.12_6 Lightweight secure web server
hicolor-icon-theme-0.17_3 Standard icon theme called hicolor
hostname-3.21_6 hostname utility
hotplug2stdout-1.2.1_6 Read kernel uevents write them to stdout.
htop-3.3.0_1 Interactive process viewer
hunspell-1.7.2_1 Spell checker and morphological analyzer
hunspell-da_DK-2.4_2 Danish da_DK dictionary for hunspell
hunspell-de_DE-20170112_2 German (Germany) dictionary for hunspell
hunspell-el_GR-0.4.0_2 Greek el_GR dictionary for hunspell
hunspell-es_ES-2.8_1 Spanish dictionary for hunspell
hunspell-fr_FR-7.0_2 French dictionary for hunspell
hunspell-hr_HR-20030928_3 Croatian (Croatia) dictionary for hunspell
hunspell-it_IT-4.2_2 Italian dictionary for hunspell
hunspell-nl_NL-2.20.19_1 Dutch nl_NL dictionary for hunspell
hunspell-pl_PL-20220801_1 Polish dictionary for hunspell
hunspell-ro_RO-3.3.10_1 Romanian dictionary for hunspell
hunspell-ru_RU-0.4.3_2 Russian dictionary for hunspell
hunspell-sl_SI-2023.01.03_1 Slovenian dictionary for hunspell
hunspell-sr_SR-20130715_1 Serbian dictionary for hunspell - cyrillic and latin
hunspell-sv_SE-2.41_2 Swedish sv_SE dictionary for hunspell
hyphen-2.8.8_3 ALTLinux hyphenation library
iceauth-1.0.9_1 ICE protocol utility
iconfinder-1.4_1 Find icons in your system
icu-73.2_2 Robust and fully-featured Unicode libraries
icu-libs-73.2_2 Robust and fully-featured Unicode libraries - shared libs
ifplugd-0.25_6 A daemon to automatically configure a ethernet device on state change
ifplugd-old-0.18_6 ethernet activity sniffer
inih-58_1 Simple ini file parser library
inkscape-1.3.2_2 Vector-based drawing program
inotify-tools-3.20.11.0_1 Provides a simple interface to inotify
iproute2-6.7.0_1 IP Routing Utilities
iptables-1.8.10_1 Linux IPv[46] packet filtering ruleset
iso-codes-4.16.0_1 List of country, language and currency names
iw-5.19_1 Utility for nl80211 based CLI configuration of wireless devices
jack-1.9.22_1 JACK Audio Connection Kit low-latency sound server (pro audio)
jansson-2.14_1 Library for encoding, decoding and manipulating JSON data
jasper-2.0.25_1 Software-based reference implementation of the JPEG-2000 codec
jbigkit-libs-2.2_2 Data compression library/utilities for bi-level high-resolution images - shared libraries
jimtcl-0.77_6 no description
json-c-0.17_1 JSON implementation in C
json-glib-1.8.0_1 JSON parser for GLib-based libraries and applications
jsoncpp-1.9.5_1 JSON implementation in C++
jwm-2.4.2_6 Joes Window Manager
jwm3_theme_black-deep-20220319_1 deep black jwm theme
jwm3_theme_easyblue-20220415_1 jwm window manager theme, blue
jwm3_theme_easygrey-20240117_1 flat grey theme for jwm
jwm3_theme_light-orange-brown-20230208_1 light orange-brown jwm theme
jwm3_theme_peachy-darkbrown-20220210_1 peachy-darkbrown theme for JWM window manager
jwm3_theme_peachy-red-20220210_1 peachy-red theme for JWM window manager
jwmthememaker-1.9.8.22_1 JWM Theme Maker, by trio. fixed for quirky
keyutils-1.6.3_1 Linux Key Management Utilities
kmod-31_1 Linux kernel module handling
ktsuss-20140304_6 ktsuss is a graphical version frontend of su written in C and GTK 2
lame-3.100_2 Fast, high quality MP3 encoder
lcms-1.19_11 Light Color Management System -- a color management library
lcms2-2.16_2 Small-footprint color management engine, version 2
ldb-2.3.2_3 LDAP-like database from samba
leafpad-0.8.19_1 GTK+ Simple text editor
less-643_1 Pager program similar to more(1)
lib2geom-1.3_1 Easy to use 2D geometry library for c++
libICE-1.1.1_1 Inter Client Exchange (ICE) library for X
libSM-1.2.4_1 X Session Management Library
libX11-1.8.7_2 Base X libraries from Xorg
libXScrnSaver-1.2.4_1 X11 Screen Saver Library
libXau-1.0.11_1 Authorization Protocol for X
libXaw-1.0.15_1 X Athena Widgets Library
libXcomposite-0.4.6_1 X Composite Library
libXcursor-1.2.1_2 Client-side cursor loading library for X
libXdamage-1.1.6_1 Xdamage extension Library
libXdmcp-1.1.4_1 X Display Manager Control Protocol library
libXext-1.3.6_1 X Extension library
libXfixes-6.0.1_1 Xfixes library and extension of X RandR from modular X.org
libXfont2-2.0.6_1 X font 2 Library
libXft-2.3.8_1 Library for configuring and customizing font access
libXi-1.8.1_1 X Input extension library
libXinerama-1.1.5_1 X PanoramiX extension library
libXmu-1.1.4_1 X Miscellaneous Utilities library
libXp-1.0.4_1 X Print Service Extension Library
libXpm-3.5.17_1 X PixMap Library from modular Xorg X11
libXpresent-1.0.1_1 XPresent extension C library
libXrandr-1.5.4_1 X RandR Library from X.org
libXrender-0.9.11_1 X Render Library
libXres-1.2.2_1 X Resource Information Extension Library
libXt-1.3.0_1 X Toolkit Intrinsics library
libXtst-1.2.4_1 X Tst Library
libXv-1.0.12_1 Xv Extension library
libXvMC-1.0.13_1 XVideo Motion Compensation Library
libXxf86vm-1.1.5_1 Library for the XFree86-VidMode X extension
libabw-0.1.3_1 Library that parses the file format of AbiWord documents
libadwaita-1.4.3_1 GTK4 building blocks for modern adaptive applications
libaio-0.3.113_1 Linux-native asynchronous I/O facility (aio) library
libao-1.2.2_2 Cross-platform audio output library
libaom-3.8.1_1 AV1 Codec library implementation
libarchive-3.7.2_1 Library to read/write several different streaming archive formats
libargon2-20190702_3 Password hashing library
libart-2.3.21_7 High-performance 2D graphics library
libaspell-0.60.8_5 Spell checker with good multi-language support - library
libass-0.17.1_1 Portable library for SSA/ASS subtitles rendering
libassuan-2.5.6_1 IPC library used by some GnuPG related software
libasyncns-0.8_9 C library for executing name service queries asynchronously
libatomic-13.2.0_2 GNU Compiler Collection - Atomics library
libavcodec-4.4.4_6 FFmpeg codec library
libavdevice-4.4.4_6 FFmpeg device handling library
libavfilter-4.4.4_6 FFmpeg audio/video filter library
libavformat-4.4.4_6 FFmpeg file format library
libavresample-4.4.4_6 FFmpeg audio resampling library
libavutil-4.4.4_6 FFmpeg utility library
libblkid-2.39.3_1 Library to handle device identification
libbluray-1.3.4_1 Library to access Blu-Ray disks for video playback
libboost_atomic-1.83.0_4 Free peer-reviewed portable C++ source libraries - libboost_atomic
libboost_chrono-1.83.0_4 Free peer-reviewed portable C++ source libraries - libboost_chrono
libboost_context-1.83.0_4 Free peer-reviewed portable C++ source libraries - libboost_context
libboost_date_time-1.83.0_4 Free peer-reviewed portable C++ source libraries - libboost_date_time
libboost_filesystem-1.83.0_4 Free peer-reviewed portable C++ source libraries - libboost_filesystem
libboost_iostreams-1.83.0_4 Free peer-reviewed portable C++ source libraries - libboost_iostreams
libboost_locale-1.83.0_4 Free peer-reviewed portable C++ source libraries - libboost_locale
libboost_program_options-1.83.0_4 Free peer-reviewed portable C++ source libraries - libboost_program_options
libboost_system-1.83.0_4 Free peer-reviewed portable C++ source libraries - libboost_system
libboost_thread-1.83.0_4 Free peer-reviewed portable C++ source libraries - libboost_thread
libbpf-1.3.0_1 Library for working with (e)BPF
libbs2b-3.1.0_3 Audiofilter for headphones
libbsd-0.11.8_1 Provides useful functions commonly found on BSD system
libcanberra-0.30_12 XDG Sound Theme and Name Specification library implementation
libcanberra-gtk3-0.30_12 XDG Sound Theme and Name Specification library implementation - GTK+ (3.x) support
libcap-2.69_2 POSIX.1e capabilities suite
libcap-ng-0.8.4_1 Alternate POSIX capabilities library
libcap-progs-2.69_2 POSIX.1e capabilities suite - utilities
libcddb-1.3.2_9 Library to access data on a CDDB server
libcdio-2.1.0_1 CD-ROM access library
libcdio-paranoia-10.2+2.0.1_1 CD paranoia utility/libraries from libcdio
libcdparanoia-10.2_15 CDDA reading utility with extra data verification features - runtime library
libcdr-0.1.7_6 Corel Draw file format importer library
libcloudproviders-0.3.5_1 DBus API for cloud storage sync clients to expose their services
libcolord-1.4.6_2 System daemon for managing color devices - runtime library
libconfig-1.7.3_1 C Configuration File Library
libcotp-3.0.0_1 Library for generating TOTP and HOTP
libcroco-0.6.13_1 Toolkit to parse and manipulate CSS (Cascading Style Sheets)
libcrypto1.1-1.1.1t_2 Toolkit for Secure Sockets Layer and Transport Layer Security - crypto library
libcrypto3-3.1.5_1 Toolkit for Secure Sockets Layer and Transport Layer Security - crypto library
libcups-2.4.7_4 Common Unix Printing System - client runtime shared libraries
libcups-filters-1.28.17_4 OpenPrinting CUPS Filters - shared library
libcurl-8.6.0_1 Multiprotocol file transfer library
libdaemon-0.14_9 Lightweight C library that eases the writing of UNIX daemons
libdatrie-0.2.13_1 Implementation of double-array structure for representing trie
libdav1d-1.3.0_1 Small and fast AV1 Decoder - runtime library
libdb-5.3.28_8 Berkeley DB embedded database system - C shared libraries
libde265-1.0.12_1 Open h.265 video codec implementation
libdebuginfod-0.190_1 Utilities to handle ELF object files - debuginfod library
libdecor-0.1.1_1 Client-side decorations library for Wayland client
libdjvulibre-3.5.28_2 Utilities for the DjVu image format - runtime libraries
libdmx-1.1.4_1 DMX Extension for X
libdrm-2.4.120_1 Userspace interface to kernel DRM services
libdvdcss-1.4.3_1 Simple library designed for accessing DVDs
libdvdnav-6.1.1_1 Library to navigate DVDs
libdvdread-6.1.3_1 DVD access library
libe-book-0.1.3_13 Import reflowable e-book formats
libedit-20230828.3.1_2 Port of the NetBSD Command Line Editor Library
libefivar-38_1 Library to manipulate EFI variables
libelf-0.190_1 Utilities to handle ELF object files - runtime library
libelogind-252.9_2 Standalone logind fork - elogind library
libepoxy-1.5.10_1 Library for handling OpenGL function pointer management for you
libepubgen-0.1.1_2 EPUB generator for librevenge
libetonyek-0.1.10_2 Library to interpret and import Apple Keynote presentations
libev-4.33_1 High-performance event loop loosely modelled after libevent
libevdev-1.13.1_1 Wrapper library for evdev devices
libevent-2.1.12_3 Abstract asynchronous event notification library
libevince-44.3_1 GNOME Document viewer for multiple document formats - runtime libraries
libexif-0.6.24_1 EXIF file library
libexttextcat-3.4.6_1 N-Gram-Based Text Categorization library
libfbclient3-3.0.6.33328_2 Relational database offering many ANSI SQL standard features (V3) - client libraries
libfdisk-2.39.3_1 Library for fdisk(8)
libffi-3.3_2 Library supporting Foreign Function Interfaces
libfftw-3.3.10_2 Library for computing the discrete Fourier transform (DFT) - runtime libraries
libflac-1.4.3_1 Free Lossless Audio Codec - shared libraries
libfluidsynth-2.3.4_1 Real-time software synthesizer based on the SoundFont 2 specifications - runtime library
libfontenc-1.1.7_1 Fontenc Library from X.org
libfreehand-0.1.2_3 Parser for Aldus/Macromedia/Adobe FreeHand documents
libgbm-23.3.5_3 Mesa Generic buffer management API - runtime
libgcc-13.2.0_2 GNU Compiler Collection - GCC library
libgcrypt-1.10.2_1 GNU cryptographic library
libgfortran-13.2.0_2 GNU Compiler Collection - Fortran library
libgirepository-1.76.1_3 Library for handling GObject introspection data (runtime library)
libgit2-1.4.5_6 the Git linkable library
libglade-2.6.4_6 no description
libglapi-23.3.5_3 Free implementation of the GL API - shared library
libglvnd-1.7.0_1 GL Vendor-Neutral Dispatch library
libgme-0.6.3_1 Video game music file emulation/playback library
libgomp-13.2.0_2 GNU Compiler Collection - OpenMP v4.0 library
libgpg-error-1.47_1 Library for error values used by GnuPG component
libgpgme-1.23.1_2 GnuPG Made Easy - library
libgphoto2-2.5.31_1 Digital camera access library
libgphoto2-udev-rules-2.5.31_1 Digital camera access library - udev rules
libgraphicsmagick-1.3.40_1 GraphicsMagick image manipulation libraries
libgs-10.02.1_1 Interpreter for the PostScript language - runtime shared library
libgsf-1.14.52_1 Structured File Library
libgsm-1.0.22_2 GSM 06.10 lossy speech compression
libgtkhtml-2.12_6 A HTML engine for GNOME2
libgudev-238_1 Library providing GObject bindings for libudev
libguile-2.2.7_3 Portable, embeddable Scheme implementation written in C - runtime library
libgusb-0.4.8_1 GLib wrapper around libusb1
libgxps-0.3.2_2 GObject base library for XPS documents
libhandy-0.0.13_3 GTK+3 building blocks for modern adaptive applications
libhandy1-1.8.3_1 GTK+3 building blocks for modern adaptive applications
libharfbuzz-8.3.0_1 OpenType text shaping engine - runtime library
libheif-1.17.5_1 ISO/IEC 23008-12:2017 HEIF file format decoder and encoder
libhistory8-8.2.001_1 GNU Readline Library - history library
libhunspell1.7-1.7.2_1 Spell checker and morphological analyzer - runtime library
libical-3.0.17_1 Reference implementation of the iCalendar data type and format
libid3tag-0.15.1b_8 ID3 tag library, part of MAD (MPEG Audio Decoder)
libidn-1.42_1 Internationalized string handling library
libidn2-2.3.4_1 Internationalized string handling library
libieee1284-0.2.11_4 A library to query devices connected in parallel port
libijs-10.02.1_1 Interpreter for the PostScript language - IJS runtime shared library
libimagequant-4.3.0_1 Palette quantization library
libinotify-tools-3.20.11.0_1 Provides a simple interface to inotify - library files
libinput-1.25.0_1 Provides handling input devices in Wayland compositors and X
libixion-0.19.0_1 General purpose formula parser and interpreter
libjack-1.9.22_1 JACK Audio Connection Kit low-latency sound server (pro audio) - runtime library
libjasper-2.0.25_1 Software-based reference implementation of the JPEG-2000 codec - shared library
libjbig2dec-0.20_1 Decoder implementation of the JBIG2 image compression format - runtime library
libjpeg-turbo-3.0.1_1 Derivative of libjpeg which uses SIMD instructions
libkeyutils-1.6.3_1 Linux Key Management Utilities - runtime library
libkmod-31_1 Linux kernel module handling - runtime shared library
libksba-1.6.5_1 CMS and X.509 access library
liblangtag-0.6.7_1 Interface library to access tags for identifying languages
libldap-2.6.6_3 OpenLDAP (Lightweight Directory Access Protocol) library
libldns-1.8.3_2 Modern DNS/DNSSEC library
liblilv-0.24.12_4 Simple yet powerful C API for using LV2 plugins - Runtime library
libllvm15-15.0.7_4 LLVM Compiler Infrastructure Project - Version 15 - runtime library
libllvm17-17.0.6_2 LLVM Compiler Infrastructure Project - Version 17 - library
liblrdf-0.6.1_2 Lightweight RDF library with special support for LADSPA plugins
libltdl-2.4.7_5 Runtime libraries for GNU Libtool Dynamic Module Loader
liblz4-1.9.4_1 LZ4 compression library
liblzma-5.4.6_1 XZ-format compression library
libmad-0.15.1b_10 High-quality MPEG audio decoder
libmagic-5.45_1 File type identification library
libmariadbclient-11.1.2_2 Fast SQL database server, drop-in replacement for MySQL - client library
libmcpp-2.7.2_8 Portable C preprocessor - Runtime library
libmd-1.1.0_1 Message Digest functions from BSD systems
libmikmod-3.3.11.1_1 MikMod Sound Library
libmm-glib-1.18.12_1 Mobile broadband modem management service - GLib library
libmng-2.0.3_2 Multiple-image Network Graphics (MNG) reference library
libmnl-1.0.5_1 Minimalistic user-space library oriented to Netlink developers
libmodplug-0.8.9.0_1 A MOD playing library
libmount-2.39.3_1 Library for mount(8)
libmpc-1.3.1_1 C library for the arithmetic of complex numbers
libmpg123-1.32.3_1 Fast console MPEG audio decoder/player - Runtime library
libmspub-0.1.4_11 Library for parsing the mspub file structure
libmtp-1.1.21_1 Library for Microsoft's Media Transfer Protocol (MTP)
libmwaw-0.3.22_1 Import library for legacy Mac documents
libmysofa-1.3.1_1 Reader for AES SOFA files to get better HRTFs
libndp-1.8_1 Library for Neighbor Discovery Protocol
libnetfilter_conntrack-1.0.9_1 Library providing an API to the in-kernel connection tracking table
libnetpbm-11.05.02_1 Toolkit for manipulation of graphic images - runtime libraries
libnewt-0.52.23_6 A library for text mode user interfaces
libnfnetlink-1.0.2_1 Low-level library for netfilter kernel/userspace communication
libnftnl-1.2.6_1 Low-level netlink interface to nf_tables
libnice-0.1.21_2 Implementation of the IETF's draft ICE (for P2P UDP data streams)
libnl-1.1.4_4 Library for applications dealing with netlink sockets
libnl3-3.9.0_1 Netlink Protocol Library Suite
libnotify-0.8.3_1 Desktop notification library
libnsl-2.0.1_1 Public client interface for NIS(YP) and NIS+
libnumbertext-1.0.11_1 Language-neutral NUMBERTEXT and MONEYTEXT for LibreOffice Calc
libnuspell-5.1.3_1 C++ spell checking library
libodfgen-0.1.8_1 Library for generating documents in Open Document Format
libogg-1.3.5_1 Ogg bitstream file format library
liboil-0.3.17_6 Library of Optimized Inner Loops, CPU optimized functions
libopenal-1.23.1_1 Cross-platform 3D audio library
libopenjpeg-1.5.2_3 Open-source JPEG 2000 codec written in C language - library files
libopenjpeg2-2.5.0_2 Open-source JPEG 2000 codec written in C language (Version 2) - library files
liborcus-0.19.2_1 Library for processing spreadsheet documents
libpagemaker-0.0.4_2 Parses Aldus/Adobe PageMaker documents
libpaper-1.1.29_1 Library for handling paper characteristics
libparted-3.6_1 GNU Parted disk partition resizing program - shared library
libpcap-1.10.4_1 System-independent interface for user-level packet capture
libpciaccess-0.18_1 X11 PCI Access library
libpcre-8.45_3 Perl Compatible Regular Expressions - shared libraries
libpcre2-10.42_1 Perl Compatible Regular Expressions (2nd version) - shared libraries
libpcsclite-2.0.1_2 Middleware to access a smart card using SCard API (PC/SC) - library files
libpipewire-1.0.3_1 Server and user space API to deal with multimedia pipelines - pipewire library
libplacebo-5.264.1_1 Reusable library for GPU-accelerated video/image rendering
libplist-2.2.0_4 Apple Property List library
libpng-1.6.42_1 Library for manipulating PNG images
libpng12-1.2.57_6 PNG image format decoding library
libpoppler-23.12.0_1 PDF rendering library - poppler runtime library
libpostproc-4.4.4_6 FFmpeg video postprocessing library
libpotrace-1.16_2 Transforming bitmaps into vector graphics - runtime library
libprotobuf-24.1_1 Protocol buffers C++ library
libprotoc-24.1_1 Protocol buffers compiler library
libproxy-0.4.18_3 Library handling all the details of proxy configuration
libpsl-0.21.5_1 Public Suffix List library functions
libptytty-2.0_1 Library for pty/tty/utmp/wtmp/lastlog handling
libpulseaudio-16.1_1 Featureful, general-purpose sound server - shared libraries
libpyldb-util-2.3.2_3 LDAP-like database from samba - Python3 utility library
libpytalloc-util-2.4.2_1 Hierarchical pool based memory allocator with destructors - Python3 utility library
libqpdf-11.6.4_1 Content-Preserving PDF Transformation System - shared library
libqrencode-4.1.1_1 Library for encoding data in a QR Code symbol - runtime library
libquadmath-13.2.0_2 GNU Compiler Collection - quadmath library
libqxp-0.0.2_9 Parser for QuarkXPress file format documents
libraptor-2.0.16_1 Raptor RDF Syntax Library - Runtime libraries
librasqal-0.9.33_3 RDF Query Library - Runtime libraries
libraw1394-2.1.2_1 Provides an API to the Linux IEEE1394 (FireWire) driver
librdf-1.0.17_6 Redland Resource Description Framework (RDF) - library
libreadline8-8.2.001_1 GNU Readline Library
libreoffice-calc-7.6.4.1_1 Productivity suite - Spreadsheet
libreoffice-common-7.6.4.1_1 Productivity suite - Common files
libreoffice-draw-7.6.4.1_1 Productivity suite - Drawing application
libreoffice-gnome-7.6.4.1_1 Productivity suite - GNOME integration
libreoffice-i18n-af-7.6.4.1_1 Productivity suite - Afrikaans language pack
libreoffice-i18n-am-7.6.4.1_1 Productivity suite - Amharic language pack
libreoffice-i18n-ar-7.6.4.1_1 Productivity suite - Arabic language pack
libreoffice-i18n-as-7.6.4.1_1 Productivity suite - Assamese language pack
libreoffice-i18n-de-7.6.4.1_1 Productivity suite - German language pack
libreoffice-i18n-el-7.6.4.1_1 Productivity suite - Greek language pack
libreoffice-i18n-en-GB-7.6.4.1_1 Productivity suite - English (UK) language pack
libreoffice-i18n-en-US-7.6.4.1_1 Productivity suite - English (US) language pack
libreoffice-i18n-es-7.6.4.1_1 Productivity suite - Spanish language pack
libreoffice-i18n-fr-7.6.4.1_1 Productivity suite - French language pack
libreoffice-i18n-pt-7.6.4.1_1 Productivity suite - Portuguese language pack
libreoffice-i18n-ru-7.6.4.1_1 Productivity suite - Russian language pack
libreoffice-i18n-tr-7.6.4.1_1 Productivity suite - Turkish language pack
libreoffice-impress-7.6.4.1_1 Productivity suite - Presentation application
libreoffice-writer-7.6.4.1_1 Productivity suite - Word processor
librevenge-0.0.5_1 Library for REVerses ENGineered formats filters
librist-0.2.7_1 Reliable Internet Stream Transport (RIST)
librpm-4.18.1_2 Red Hat Package Management Utils - rpm library
librpmbuild-4.18.1_2 Red Hat Package Management Utils - rpmbuild library
librpmio-4.18.1_2 Red Hat Package Management Utils - rpmio library
librpmsign-4.18.1_2 Red Hat Package Management Utils - rpmsign library
librsvg-2.57.0_1 SVG library for GNOME
librsvg-utils-2.57.0_1 SVG library for GNOME - utilities
librtmp-2.4.20161210_10 Toolkit for RTMP streams - shared library
librubberband-3.3.0_1 Time-stretching and pitch-shifting audio library - Runtime libraries
libsamplerate-0.2.2_1 Sample Rate Converter for audio
libsane-1.2.1_1 Scanner Access Now Easy - runtime shared library
libsasl-2.1.28_2 Cyrus SASL - runtime shared libraries
libseccomp-2.5.5_1 High level interface to the Linux Kernel's seccomp filter
libsecret-0.21.3_1 GObject based library for accessing the Secret Service API
libsensors-3.6.0_1 Library to read temperature/voltage/fan sensors
libserd-0.32.2_1 Lightweight C library for RDF syntax - Runtime library
libsharpyuv-1.3.2_1 Library to expose libwebp's sharpyuv functionality
libsigc++-2.12.0_1 Type-safe callback system for C++ programs
libsigsegv-2.14_1 Handling page faults in user mode
libsmartcols-2.39.3_1 Table or Tree library from util-linux
libsndfile-1.2.2_1 C library for reading and writing files containing sampled sound
libsndio-1.9.0_1 Small audio and MIDI framework part of the OpenBSD project -- library
libsodium-1.0.19_1 Modern and easy-to-use crypto library
libsord-0.16.16_1 Lightweight C library for storing RDF data in memory - Runtime library
libsoup-2.74.0_1 HTTP library implementation in C
libsoup-gnome-2.74.0_1 HTTP library implementation in C - GNOME libraries
libsoxr-0.1.3_2 SoX resampler library
libspectre-0.2.12_1 Small library for rendering Postscript documents
libspeex-1.2.1_1 Free codec for free speech - shared libraries
libspnav-1.1_1 Open source alternative to 3DConnextion drivers
libsrt-1.5.3_1 Secure, Reliable, Transport - development files
libsrtp-2.5.0_2 Library implementing SRTP, the Secure Real-time Transport Protocol
libssh-0.10.6_1 Multiplatform C library implementing the SSH v2 protocol
libssh2-1.11.0_2 Library implementing the SSH2 protocol
libssl1.1-1.1.1t_2 Toolkit for Secure Sockets Layer and Transport Layer Security - SSL/TLS library
libssl3-3.1.5_1 Toolkit for Secure Sockets Layer and Transport Layer Security - SSL/TLS library
libstdc++-13.2.0_2 GNU Compiler Collection - Standard C++ Library
libsvt-av1-1.7.0_1 AV1-compliant encoder/decoder library core - library files
libswresample-4.4.4_6 FFmpeg video resampling library
libswscale-4.4.4_6 FFmpeg video scaling library
libsysfs-2.1.0_7 Library to query system device information exposed through sysfs
libsystem-0.3.1_6 A system library needed by surfer web browser.
libtasn1-4.19.0_1 ASN.1 structure parser library
libtdb-1.4.9_2 Trivial Database, similar to GDBM but allows simultaneous commits - shared libraries
libtermkey-0.22_1 Library for processing keyboard entry from terminal-based programs
libthai-0.1.29_1 Thai language support routines
libtheora-1.1.1_8 Theora Video Compression Codec
libtirpc-1.3.4_1 Transport Independent RPC library (SunRPC replacement)
libtommath-1.2.1_1 Portable number theoretic multiple-precision integer library
libtool-2.4.7_5 Generic library support script
libtracker-3.6.0_1 Personal search tool and storage system - shared libraries
libtubo-4.5.2_6 Library needed by xfdiff-cut
libunbound-1.19.1_1 Validating, recursive, and caching DNS resolver - shared library
libunistring-1.0_1 Library for manipulating Unicode strings and C strings
libunwind-1.8.0_1 Library to determine the call-chain of a program
libusb-1.0.27_1 Library which allows userspace access to USB devices
libusb-compat-0.1.8_1 libusb-0.1 compatibility library
libusbmuxd-2.0.2_1 USB Multiplex Daemon library
libuuid-2.39.3_1 UUID library
libva-2.20.0_1 Video Acceleration (VA) API
libvala-0.56.14_1 Compiler for the GObject type system - vala shared library
libvamp-plugin-sdk-2.10.0_1 Vamp audio analysis plugin system - Runtime libraries
libvdpau-1.5_1 Video Decode and Presentation API for UNIX
libvdpau-va-gl-0.4.2_2 VDPAU driver with VA-API/OpenGL backend
libvidstab-1.1.0_2 Video stabilization library
libvisio-0.1.7_8 Library for reading and converting MS Visio diagrams
libvisual-0.4.2_1 Abstraction library for audio visualisation plugins
libvoikko-4.3.2_1 Free linguistic software and data for Finnish
libvorbis-1.3.7_1 The Vorbis General Audio Compression Codec
libvpx-1.13.1_1 VP8 and VP9 video codec
libvpx-tools-1.13.1_1 VP8 and VP9 video codec - tools
libwacom-2.10.0_1 Library to identify wacom tablets
libwebp-1.3.2_1 WebP image format
libwmf-0.2.8.4_18 Library for reading and converting WMF (Windows Meta Files)
libwpd-0.10.3_1 Library for importing WordPerfect documents
libwpg-0.3.3_1 Library for importing WordPerfect Graphics
libwps-0.4.12_1 Library for importing Microsoft Works documents
libx86-1.1_8 Library for making real-mode x86 calls
libxatracker-23.3.5_3 Mesa XA tracker interface library
libxbps-0.59.2_3 XBPS package system utilities - runtime library
libxcb-1.16_1 X protocol C-language Binding
libxcrypt-4.4.36_3 Modern library for one-way hashing of passwords
libxcrypt-compat-4.4.36_3 Modern library for one-way hashing of passwords - legacy compatibility
libxcvt-0.1.2_1 VESA CVT standard timing modelines generator
libxkbcommon-1.6.0_2 Library to handle keyboard descriptions
libxkbcommon-tools-1.6.0_2 Library to handle keyboard descriptions - utilities
libxkbcommon-x11-1.6.0_2 Library to handle keyboard descriptions - X11 support
libxkbfile-1.1.3_1 Xkbfile Library from X.org
libxkbregistry-1.6.0_2 XKB API to query available rules, models, layouts, variants and options
libxml2-2.11.4_6 Library providing XML and HTML support
libxmlb-0.3.15_1 Library to help create and query binary XML blobs
libxshmfence-1.3.2_1 X Shared memory 'SyncFence' synchronization primitive
libxslt-1.1.39_2 XSLT parser library from the GNOME project
libxxHash-0.8.2_1 Fast non-cryptographic hashing algorithm - library
libyaml-0.2.5_1 Fast YAML 1.1 parser and emitter library
libzbar-0.23.1_7 Barcode reading library and application - library files
libzstd-1.5.5_2 Fast real-time compression algorithm
limine-4.20231006.0_6 x86x86_64 BIOSUEFI bootloader
listres-1.0.5_1 List resources in Xaw widgets
lm_sensors-3.6.0_1 Utilities to read temperature/voltage/fan sensors
lmarbles-1.0.8164_1 Atomix-like enhanced puzzle game.
lmdb-0.9.31_1 Lightning Memory-Mapped Database Manager
lpsolve-5.5.2.5_2 Mixed Integer Linear Programming (MILP) solver
lua52-5.2.4_12 Powerful, fast, lightweight, embeddable scripting language (5.2.x)
lua53-5.3.6_1 Powerful, fast, lightweight, embeddable scripting language (5.3.x)
lxrandr-0.3.2_2 LXDE Monitor configuration tool
lxtask-0.1.10_1 LXDE Task Manager
lxterminal-0.4.0_1 LXDE Terminal emulator
lz4-1.9.4_1 LZ4 compression utilities
lzlib-1.14_1 Compression library for the lzip file format
lzo-2.10_2 Portable lossless data compression library
maag-1.61_1 Make an Animated GIF
makedepend-1.0.7_1 Dependency generator for makefiles
mbedtls-2.16.12_1 Portable cryptographic TLS library
mcpp-2.7.2_8 Portable C preprocessor
mdview-2023.12.12_6 Simple markdown viewer using only gtk
mesa-23.3.5_3 Open source implementation of OpenGL and Vulkan
mesa-ati-dri-23.3.5_3 Mesa DRI drivers for ATI GPUs (transitional dummy package)
mesa-dri-23.3.5_3 Mesa DRI drivers
mesa-intel-dri-23.3.5_3 Mesa DRI drivers for Intel GPUs (transitional dummy package)
mesa-nouveau-dri-23.3.5_3 Mesa DRI drivers for NVIDIA GPUs (transitional dummy package)
mesa-vaapi-23.3.5_3 Mesa VA-API drivers
mesa-vdpau-23.3.5_3 Mesa VDPAU drivers
mesa-vulkan-intel-23.3.5_3 Mesa Intel Vulkan driver
mesa-vulkan-radeon-23.3.5_3 Mesa Radeon Vulkan driver
metamail-2.754_6 MIME decoder
mingetty-1.08_6 Compact getty terminal handler for virtual consoles only
minixcal-1.1.1_6 Calendar applet written in gtk2. Excellent as tray applet
mirdir-2.1_6 Compare two directory trees copy differences.
mit-krb5-libs-1.21.2_3 MIT Kerberos 5 implementation - runtime libraries
mkfontscale-1.2.2_1 X11 Scalable Font Index Generator
mobile-broadband-provider-info-20220511_1 Database of mobile broadband service providers
modem-stats-1.0.1_6 Send Hayes commands to a serial port.
mped-3.3.17_6 Lightweight CLI text editor for programmers
mpfr-4.2.1_1 Library for multiple-precision floating-point computations
mplayer_codecs_basic-200710078664_1 codecs taken from windows, for linux x86_64
mpscan-0.1.0_6 Parallel network scanner that checks for open ports
mpv-0.36.0_4 Video player based on MPlayer/mplayer2
mtdev-1.1.6_1 Multitouch Protocol Translation Library
mtools-4.0.43_1 Collection of utilities to access MS-DOS disks
mtpaint-3.50.09_2 Simple GTK painting program
mtr-0.95_2 Combines the functionality of traceroute and ping into one tool
mythes-1.2.4_5 Simple thesaurus that uses a structured text data
nano-7.2_1 GNU nano text editor
nbtscan-1.0.35_6 Scans for open NETBIOS nameservers on a local or remote TCPIP network.
ncurses-6.4_2 System V Release 4.0 curses emulation library
ncurses-base-6.4_2 System V Release 4.0 curses emulation library - base terminfo files
ncurses-libs-6.4_2 System V Release 4.0 curses emulation library -- shared libraries
ncurses-libtinfo-libs-6.4_2 System V Release 4.0 curses emulation library - libtinfo.so symlink
ncurses-term-6.4_2 System V Release 4.0 curses emulation library - full terminal descriptions
nenscript-1.13.3_6 Converts text files to PostScript.
net-tools-2.10_1 Basic networking tools
netpbm-11.05.02_1 Toolkit for manipulation of graphic images
nettle-3.9.1_1 Low-level cryptographic library
network-manager-applet-1.8.20_6 network manager tray applet
network-tray-3.5_6 Tray applet for Puppy and derivatives show network activity
newt-0.52.21_7 Library for color text mode, widget based user interfaces
nghttp2-1.59.0_1 HTTP/2 C Library
notecase-1.9.81_6 A hierarchical text notes manager.
notification-daemon-3.20.0_2 Shows notification messages on the desktop
npth-1.6_1 New portable threads library
nspr-4.35_1 NetScape Portable Runtime
nss-3.98_1 Mozilla Network Security Services
ntfs-3g-2022.10.3_1 Stable Read/Write NTFS Driver in userspace
ntp-4.2.815_6 Network Time Protocol daemon and utilities
numlockx-1.2_5 Activate NumLock at startup
ocl-icd-2.3.2_2 Generic OpenCL ICD loader/demultiplexer
ofono-1.31_3 Infrastructure for building mobile telephony (GMS/UTMS) applications
oniguruma-6.9.9_1 Multi-charset regular expressions library
openblas-0.3.26_1 Optimized BLAS (Basic Linear Algebra Subprograms) based on GotoBLAS2
openjpeg-1.5.2_3 Open-source JPEG 2000 codec written in C language
openssh-9.6p1_2 OpenSSH free Secure Shell (SSH) client and server implementation
openssl-3.1.5_1 Toolkit for Secure Sockets Layer and Transport Layer Security
opkg-utils-0.5.0_6 Additional utilities for the opkg package manager
opus-1.4_1 Totally open, royalty-free, highly versatile audio codec
orc-0.4.37_1 Oild Runtime Compiler
osmo-0.2.12_6 diary organiser planner
ostree-2024.3_1 Operating system and container binary deployment and upgrades
p11-kit-0.25.0_1 Provides a way to load and enumerate PKCS#11 modules
pa-applet-202111062_6 no description
pam-libs-1.5.3_4 Flexible mechanism for authenticating users - runtime libraries
pango-1.50.14_1 Library for layout and rendering of text
pango-xft-1.50.14_1 Library for layout and rendering of text - X font rendering
pangomm-2.46.2_1 C++ bindings for the pango library
parcellite-1.2.2_6 Clipboard manager
parted-3.6_1 GNU Parted disk partition resizing program
patch-2.7.6_4 Patch files using diff output
pavucontrol-5.0_3 PulseAudio Volume Control
pburn3-3.7.181_1 Pburn CD/DVD/Blu-ray writer
pcdripper-3.9.41_1 Pcdripper CD song ripper, created by plinej
pciutils-3.10.0_1 PCI bus related utilities
pclock-0.8.21_1 pClock time tools
pcre-8.45_3 Perl Compatible Regular Expressions
pctorrent-1.72_1 torrent client gui, created by plinej
pdvdrip-1.0.01_1 dvd rip. created by plinej
peasydisc-3.7_1 PeasyDisc CD/DVD tools
peasyglue-1.9_1 Image joiner
peasypdf-4.1_1 Manipulate PDF documents
peasyport-noarch-2.2_1 Network port scanner
peasyprint-2.8_1 PeasyPrint graphic/photo printing
peasyscale-exec-1.4_6 Image scaler utility.
peasyscale-noarch-1.8_1 JPEG image resizer
peasyscan-exec-1.0.14_6 Hacked scanner utility for peasyscan package.
peasyscan-noarch-2.121_1 PeasyScan simple image scanner
perl-5.38.2_3 Practical Extraction and Report Language
pfilesearch-2.3_1 file finder engine, used by pmusic, pburn
pfind-6.32_1 pFind file finder
pflask-20180925_6 Light weight container runtime
phash-2_1 adds to rox right-click menu, calc md5sum/sha1sum of a file
picpuz-2.464_1 jigsaw puzzle
picscale-0.1_6 Scale png images from the command line.
pinentry-1.2.1_1 PIN or passphrase entry dialogs for GnuPG
pinentry-gtk-1.2.1_1 PIN or passphrase entry dialogs for GnuPG based on GTK+
pixman-0.42.2_1 Library of low-level pixel manipulation routines
pmcputemp-1.264_1 tray applet cpu temperature monitor
pmirror-0.6.21_1 Pmirror backup a directory
pmirrorget-0.2.11_1 Website File Grabber
pngoverlay-cairo-20190623_6 Overlay two 48x48 PNG images
polkit-121_1 Authorization Toolkit
poppler-23.12.0_1 PDF rendering library
poppler-cpp-23.12.0_1 PDF rendering library - C++ bindings
poppler-glib-23.12.0_1 PDF rendering library - GLib bindings
popt-1.19_1 Command line option parsing library
powerapplet-tray-3.0_6 Battery status monitor for the system tray
ppp-2.4.9_6 Point-to-Point Protocol PPP support
pprocess-2.3.2_1 Pprocess process manager
pps-tools-1.0.2_1 Tools for LinuxPPS (pulse-per-second)
precord-9.0.31_1 Precord mp3,ogg,wav recorder/player
prename-0.7_1 batch file renamer
printer-driver-samsung-1.00.39164_1 Extra filter required for Samsung printers
procps-ng-4.0.4_2 Utilities for monitoring your system and its processes
programchooser-0.3_1 used by wallpaper-setter
protobuf-c-1.4.1_3 C implementation of the Google Protocol Buffers
prun-1.31_1 Run dialog utility
pschedule-1.1.63_1 Pschedule task on time
ptooltips-0.21_1 display tooltips utility
public-suffix-2024.01.07_1 Public Suffix List
pulseaudio-16.1_1 Featureful, general-purpose sound server
pulseaudio-utils-16.1_1 Featureful, general-purpose sound server - utilities
pup-tools-20221101_6 Core utilities used in EasyOS and Puppy and derivatives
puppy-podcast-grabber-1.31_1 podcast grabber
puppyinputdetect-1.1_6 usb ps2 mouse and keyboard detection console utility.
puppyserialdetect-1.1_6 Serial mouse and modem detection console utility.
pupradio-1.2_1 pupRadio streaming audio
pupx-0.5_1 pupX X settings
pwsget-0.11_1 Pwsget secure file downloader
python3-3.12.2_2 Python programming language (3.12 series)
python3-Mako-1.2.4_2 Hyperfast and lightweight templating for Python3
python3-Markdown-3.4.4_2 Python3 implementation of John Gruber's Markdown
python3-MarkupSafe-2.1.5_1 Implements a XML/HTML/XHTML Markup safe string for Python3
python3-Pillow-10.2.0_1 Python Imaging Library (PIL) for for Python3
python3-appdirs-1.4.4_6 Python3 module for determining appropriate platform-specific dirs
python3-cairo-1.25.1_1 Python3 bindings for the cairo graphics library
python3-certifi-2022.09.24_4 Curated collection of Root Certificates
python3-cffi-1.16.0_1 C foreign function interface for Python3
python3-chardet-5.2.0_1 Universal encoding detector
python3-charset-normalizer-3.3.2_1 Encoding and language detection
python3-cssselect-1.2.0_2 CSS selectors for Python3
python3-dbus-1.3.2_2 D-Bus Python3 bindings
python3-distutils-extra-2.39_10 Enhancements to the Python3 build system
python3-gobject-3.46.0_2 Python3 bindings for GObject
python3-idna-3.6_1 Internationalized Domain Names in Applications (IDNA) for Python3
python3-lxml-4.9.3_3 Python binding for the libxml2 and libxslt libraries
python3-numpy-1.26.4_1 Fast and sophisticated array facility to Python3
python3-parsing-3.1.1_2 Python parsing module
python3-ply-3.11_8 Lex and Yacc for Python3
python3-prctl-1.7_10 Python3 interface for the Linux prctl syscall
python3-pycparser-2.21_2 Complete C99 parser in pure Python (Python3)
python3-requests-2.31.0_2 Python3 HTTP library for human beings
python3-scour-0.38.2_4 SVG scrubber (Python3)
python3-setuptools-69.0.3_1 Easily build and distribute Python3 packages
python3-six-1.16.0_4 Python 2 and 3 compatibility utilities (Python3)
python3-urllib3-1.26.12_2 HTTP library with thread-safe connection pooling
qpdf-11.6.4_1 Content-Preserving PDF Transformation System
rdesktop-1.9.0_3 Open source client for Windows Remote Desktop Services
readline-8.0.0_1 Readline meta package
recordmydesktop-0.3.8.1_4 A X11 desktop session recorder
redshift-1.11_7 Redshift adjusts the color temperature of your screen according to your surroundings
refind-0.13.3.1_6 EFI boot manager software
restarter-20190208_6 Command supervisor and restarter. Restarts a command on crash or exit.
rox-filer-20231203_6 Drag-and-drop based filemanager
rp-pppoe-3.13_6 A user-mode PPPoE client and server suite for Linux
rpcsvc-proto-1.4.1_1 Rpcsvc protocol definitions from glibc
rpm-4.18.1_2 Red Hat Package Management Utils
rshift_tray-20220102_1 redshift gui for tray
rsync-3.2.7_2 Remote fast incremental file transfer tool
rtkit-0.13_3 Realtime Policy and Watchdog Daemon
rubix-1.0.6_6 rubix is a Rubiks cube system for the LinuxX11 operating system.
run-parts-4.11.2_2 Run scripts or programs in a directory
rxvt-unicode-9.30_6 rxvt terminal clone supporting unicode
sakura-2.4.2_6 sakura is a terminal emulator based on GTK and libvte
samba-4.14.12_5 SMB/CIFS file, print, and login server for Unix
samba-cups-4.14.12_5 SMB backend for cups (transitional dummy package)
samba-libs-4.14.12_5 SMB/CIFS file, print, and login server for Unix - core libraries
sane-1.2.1_1 Scanner Access Now Easy
sbc-2.0_1 Bluetooth Subband Codec (SBC) library
scale2x-4.0_6 Scale PNG images x2 x4
scrcpy-1.24_6 Display and control your Android device
sed-4.9_1 The GNU stream editor
sessreg-1.1.3_1 Manage utmp/wtmp entries for xdm
setcolortemperature-20210313_6 Screen temperature utility
setvol-1.1_6 A simple commandline volume control.
setxkbmap-1.3.4_1 Set the keyboard map using the X Keyboard Extension
shaderc-2022.2_1 Collection of tools, libraries and tests for shader compilation
shared-mime-info-1.15_6 Shared MIME type database and specification
simple-mtpfs-0.4.064_1 fuse filesystem to mount mtp device
simple_xcursor_creator-20230727_1 Simple Xcursor Creator and Selector
slang-2.3.2_2 S-Lang programming library
smbclient-4.14.12_5 SMB/CIFS file, print, and login server for Unix - client utilities
smbnetfs-0.6.3_6 FUSE module for mounting an entire SMBNMB network in a single directory
smpeg-0.4.5_5 SDL MPEG Player Library
smproxy-1.0.7_1 X11R6 session management application
solvespace-3.1_1 Parametric 2d/3d CAD
soundtouch-2.3.2_1 SoundTouch Audio Processing Library
spandsp-0.0.6_4 Library of many DSP functions for telephony
speex-1.2.1_1 Free codec for free speech
speexdsp-1.2.1_1 Free codec for free speech - DSP
sqlite-3.44.2_2 SQL Database Engine in a C Library
squashfs-tools-4.6.1_1 Tool to create and append to squashfs filesystems
sratom-0.6.16_1 Library for serialising LV2 atoms to/from RDF (Turtle syntax)
ssh-gui-0.7.1_6 SSHGUI is a frontend for ssh.
sshpass-1.10_1 Non-interactive ssh password auth
startup-notification-0.12_11 Library for tracking application startup
sudo-sh-1.364_1 replacement for sudo
sysfsutils-2.1.0_7 System Utilities Based on Sysfs
syslinux-6.042_6 Multi-purpose linux bootloader
sysvinit-3.01_6 System-V like init
talloc-2.4.2_1 Hierarchical pool based memory allocator with destructors
tar-1.35_1 GNU tape archiver with remote magnetic tape support
tas-1.15_1 Screenshot utility
tcl-8.6.13_1 TCL scripting language
tdb-1.4.9_2 Trivial Database, similar to GDBM but allows simultaneous commits
tevent-0.11.0_3 Event system based on the talloc memory management library
tiff-4.6.0_1 Library and tools for reading and writing TIFF data files
translate-shell-0.9.7.1_1 cli language translation
trousers-0.3.15_2 Trusted Computing Software Stack for the TPM
tzdata-2024a_1 Time zone and daylight-saving time data
uchardet-0.0.8_1 Encoding detector library ported from Mozilla
ufiformat-0.9.9_6 Utility to format disk in USB floppy drive
unclutter-8_6 A small tool that hides the X cursor after a period of inactivity
unibilium-2.1.1_1 Simple, self-contained terminfo library
unifont-11.0.03_1 symbols for unknown characters
unzip-6.0_15 List, test and extract compressed files in a ZIP archive
usbutils-017_1 Linux USB utilities
util-linux-2.39.3_1 Miscellaneous linux utilities
util-linux-common-2.39.3_1 Miscellaneous linux utilities - common files
v4l-utils-1.24.1_1 Userspace tools and libraries for Video 4 Linux
vala-0.56.14_1 Compiler for the GObject type system
vcdimager-2.0.1_2 Mastering suite for authoring, disassembling and analyzing Video CDs
viewnior-1.8_2 Elegant Image Viewer
viewres-1.0.7_1 Graphical class browser for Xt
vivaldi-skel-ask-20230317_1 Download latest Vivaldi
vmaf-2.3.1_1 Perceptual video quality assessment algorithm developed by Netflix
vpm-1.3_3 XBPS package management helper for VoidLinux
vte3-0.74.2_1 Terminal widget with improved accessibility and I18N support
vte9-0.28.2_6 Virtual terminal emulator GTK widget library
vulkan-loader-1.3.261.1_1 Vulkan Installable Client Driver (ICD) loader
wag_profiles-20131225_1 wifi access gadget profile manager
wavplay-2.0_6 A simple commandline wav file player.
wayland-1.22.0_1 Core Wayland window system code and protocol
wcpufreq-0.8.4_1 CPU Frequency Scaling Tool
webrtc-audio-processing-0.3.1_1 AudioProcessing library based on Google's implementation of WebRTC
wget-1.17.1_6 Console URL download utility supporting HTTP FTP etc
wireless-regdb-20190301_1 crda firmware required by wifi drivers
wpa-supplicant-2.10_6 Client for Wi-Fi Protected Access WPA
x11perf-1.6.1_1 X11 server performance test program
x264-20191217.2245_1 Free library for encoding H264/AVC video streams
x265-3.5_1 Open Source H.265/HEVC video encoder
xarchive-0.2.8618_6 A lightweight GTK2 frontend for archives.
xauth-1.1.2_1 X authentication utility
xbacklight-1.2.3_1 Adjust backlight brightness using RandR extension
xbiff-1.0.5_1 Mailbox flag for X
xbitmaps-1.1.3_1 Common X11 bitmaps
xbps-0.59.2_3 XBPS package system utilities
xbps-triggers-0.127_1 XBPS triggers for Void Linux
xcalc-1.1.2_1 Scientific calculator for X
xcb-util-0.4.1_1 XCB utilities library
xcb-util-image-0.4.1_1 Utility libraries for XCB - XImage and XShmImage functions
xcb-util-keysyms-0.4.1_1 Utility libraries for XCB - key constants and keycode conversion
xcb-util-renderutil-0.3.10_1 Utility libraries for XCB - Render extension convenience functions
xcb-util-wm-0.4.2_1 Utility libraries for XC Binding - window-manager helpers for ICCCM
xclipboard-1.1.4_1 X clipboard client
xclock-1.1.1_1 Analog and digital clock for X
xconsole-1.0.8_1 Monitor system console messages with X
xcur2png-0.7.0_6 Converter from X cursor to PNG image.
xcursorgen-1.0.8_1 X cursor generator
xdelta3-3.1.0_6 Xdelta is a tool for differential compression
xdg-dbus-proxy-0.1.5_1 Filtering proxy for D-Bus connections
xdg-desktop-portal-1.18.2_1 Portal frontend service for Flatpak
xdg-desktop-portal-gtk-1.15.1_1 Portal backend service for Flatpak using GTK+
xdg-puppy-0.7.8_6 Menu generation utilities for window managers in Puppy Linux and EasyOS
xdialog-2.3.1_6 A utility for creating X11 dialog boxes
xditview-1.0.7_1 Display ditroff output
xdotool-1.20100416.2809_6 xdotool - command-line X11 automation tool - utilising X11 XTEST interface
xdpyinfo-1.3.4_2 Display information utility for X
xdriinfo-1.0.6_1 X DRI information utility
xev-1.2.5_1 Display X events
xf86-input-evdev-2.10.6_2 Xorg event device input driver
xf86-input-joystick-1.6.3_3 Joystick Input driver for Xorg
xf86-input-libinput-1.4.0_1 Generic input driver for the X.Org server based on libinput
xf86-input-mtrack-0.5.0_2 Xorg Multitouch Trackpad Driver
xf86-input-synaptics-1.9.2_1 Xorg synaptics touchpad input driver
xf86-input-vmmouse-13.2.0_1 Xorg VMware virtual mouse input driver
xf86-input-wacom-1.2.0_1 Xorg Wacom tablet input driver
xf86-video-amdgpu-23.0.0_1 Xorg AMD Radeon RXXX video driver (amdgpu kernel module)
xf86-video-ati-22.0.0_1 Xorg ATI Radeon video driver
xf86-video-cirrus-1.5.3_9 Xorg Cirrus Logic video driver
xf86-video-dummy-0.4.1_1 Xorg dummy video driver
xf86-video-fbdev-0.5.0_2 Xorg framebuffer video driver
xf86-video-intel-2.99.917.20210115_2 Xorg DDX Intel video driver
xf86-video-mach64-6.9.6_3 Xorg ATI Rage Pro video driver
xf86-video-mga-2.0.0_3 Xorg Matrox Graphics Adapter video driver
xf86-video-nouveau-1.0.17_2 Xorg opensource NVIDIA video driver
xf86-video-openchrome-0.6.0_3 Xorg driver for VIA IGPs
xf86-video-qxl-0.1.6_1 Xorg QXL video driver
xf86-video-r128-6.12.0_2 Xorg ATI Rage 128 video driver
xf86-video-sisusb-0.9.7_3 Xorg SiS USB video driver
xf86-video-vesa-2.6.0_1 Xorg VESA video driver
xf86-video-vmware-13.4.0_1 Modular Xorg VMware virtual video driver
xfdiff-cut-4.5.0_6 Graphical diff
xfontsel-1.1.0_1 X font selector
xgamma-1.0.7_1 Alter gamma correction
xhost-1.0.9_1 Server access control program for X
xinit-1.4.2_1 X init program
xinput-1.6.4_1 Utility to configure and test X input devices
xkbcomp-1.4.6_1 XKBD keymap compiler
xkbutils-1.0.5_1 XKBD Utilities
xkeyboard-config-2.40_1 X Keyboard Configuration Database
xkill-1.0.6_1 Kill a client by its X resource
xload-1.1.4_1 System load average display for X
xlockmore-5.311_6 A collection of screensavers and lockers for X
xmag-1.0.7_1 X utility to Magnify parts of the screen
xmessage-1.0.6_1 Display a message or query in a X window
xml2-0.564_1 xml2 executable
xmlsec1-1.3.2_1 XML Security Library is a C library based on LibXML2
xmodmap-1.0.11_1 X modmap program to modify keymaps and pointer button mappings
xorg-7.6_6 X.org meta-package
xorg-server-21.1.11_1 X11 server from X.org
xorg-server-common-21.1.11_1 X11 server from X.org- common files
xorg-server-xephyr-21.1.11_1 X server outputting to a window on a pre-existing X display
xorg-skeleton-20240129_1 x skeleton, intended to install after all x installed
xorgproto-2023.2_1 Combined X.Org X11 Protocol headers
xprop-1.2.6_1 Property displayer for X
xrandr-1.5.2_1 Primitive command line interface to RandR extension
xrdb-1.2.2_1 X server resource database utility
xrefresh-1.0.7_2 Refresh all or part of an X screen
xresprobe-0.4.25_6 Monitor resolution probe
xset-1.2.5_2 X11 user preferences utility
xsetroot-1.1.3_1 X root window parameter setting program
xsm-1.0.5_1 X Session Manager
xtools-minimal-0.66_1 Opinionated helpers for working with XBPS - minimal subset
xtrans-1.5.0_1 Network API translation layer to insulate X
xvidcore-1.3.7_1 ISO MPEG-4 compliant video codec
xvidtune-1.0.4_1 Video mode tuner for Xorg
xvinfo-1.1.5_1 Query X-Video capabilities
xwd-1.0.9_1 Dump an image of an X window
xwininfo-1.1.6_1 Query information about X windows
xxHash-0.8.2_1 Fast non-cryptographic hashing algorithm
xz-5.4.6_1 XZ compression utilities
yad-0.42.39_6 GUIs for shell scripts
ycalc-1.09.1164_1 X11based scientific calculator based on the Texas TI59 calculator.
youtube-dl-20210930_1 download youtube videos, cli utility
youtubedl-gui-0.4.3_1 YouTubeDL YouTube downloader
zarfy-0.1.0_6 A gui to libxrandr. Presents a visual representation of displays
zip-3.0_6 Create/update ZIP files compatible with pkzip
zix-0.4.2_1 C library of portability wrappers and data structures
zlib-1.3.1_1 Compression/decompression Library
zstd-1.5.5_2 Fast real-time compression algorithm - CLI tool
zxing-cpp-2.1.0_1 Multi-format 1D/2D barcode image processing library
Of those, 221 are foreign packages; PET or Kirkstone packages. This is the breakdown:
pet: 92
kirkstone: 129
void: 843
The PET and Kirkstone packages have been converted to .xbps packages, so that XBPS can install them. Of the 843 Void .xbps packages, 94 have been opened up, changes applied via "packages-templates", then rebuilt, then installed.
There are some packages that XBPS installed, that I don't want in
'rootfs'; need to work on that a bit more, before going on to
developing the '6post-process-rootfs' script.
Tags: easy
woofV populate rootfs
Continuing the "woofV" project, here is the previous post:
https://bkhome.org/news/202402/woofv-topological-sort.html
In /usr/local/woofV/rootfs, there will be these scripts:
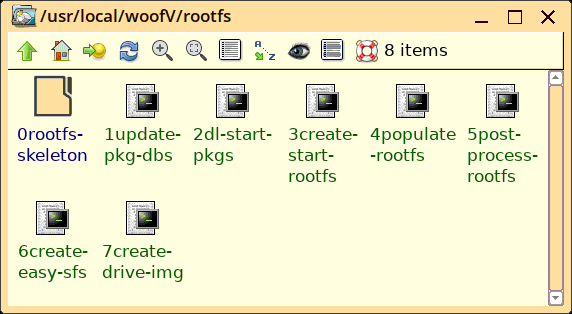
They will be executed in sequence, and I am currently working on
'4populate-rootfs'.
What this script does, is read the list of packages to be installed from file 'woof-installed-packages-dep-order', and use the XBPS package management system to install them.
They don't have to be only .xbps packages; PET .pet and Kirkstone .tar.xz packages can also be installed. These foreign packages are converted to .xbps so that XBPS can install them.
There is also a "packages-templates" section, in /usr/local/woofV/pkg-fix, which specifies that some packages may be opened up and modified before installing.
'4populate-rootfs' will populate /mnt/wkg/data/woofV/rootfs, and it is basically working. However, there are still some bugs. Will work on those tomorrow. The scripts can be found here:
https://github.com/bkauler/woofq/tree/main/easyos/easy-code/rootfs-skeleton/usr/local/woofV/rootfs
5-, 6- and 7- scripts have been roughed-out only, not yet tested
and will definitely need some work.
Tags: easy
woofV topological sort
If you have ever used Woof, the Puppy-builder, or even as a user of Puppy, you may be familiar with /root/.packages/woof-installed-packages. Or, in recent Woof-CE-built pups, it is at /var/packages/woof-installed-packages.
This has a list of the packages that are "builtin", in "Puppy DB" format. By builtin, that means that are in the SFS(s); in the case of EasyOS that is 'easy.sfs'. Here is an example of one line in that file:
argon2-20190702_3|argon2|20190702|3|Personal;lock|16K|current|argon2-20190702_3.x86_64.xbps|+glibc|Password hashing function|void|current||
Alright, here is another package, that has more dependencies:
alsa-utils-1.2.10_1|alsa-utils|1.2.10|1|BuildingBlock|1279K|current|alsa-utils-1.2.10_1.x86_64.xbps|+alsa-lib,+glibc,+libfftw,+libsamplerate,+ncurses-libs|Advanced Linux Sound Architecture (ALSA) utilities|void|current||
In woofV, I am building easy.sfs by installing each package in woof-installed-package into a folder named 'rootfs', then using the 'mksquashfs' utility to create easy.sfs.
What is different from WoofQ, is that woofV is installing each package using the XBPS package management utility 'xbps-install'. When a package is installed, 'xbps-install' will automatically install any dependencies. To get more control over this, I would like to install packages in order of dependencies.
In the case of 'alsa-utils', I want to first install 'alsa-lib', 'glibc', 'libfftw;, 'libsamplerate' and 'ncurses-libs' -- but they also need to be installed in order of dependencies. So, for the last few days, I have been trying to sort 'woof-installed-packages' into order of dependencies. Which is very difficult.
I had a little algorithm, extremely slow, but it didn't work. The problem I hit, that killed my algorithm, is that several packages in the Void repository have circular dependencies. That is, package 'A' has dependency 'B', and package 'B' has dependency 'A'.
After much puzzling, I discovered that a topological sort will do the job. This is explained on Wikipedia, but be warned, your head might hurt trying to understand it:
https://en.wikipedia.org/wiki/Topological_sorting
The 'coreutils' package has a utility 'tsort', as also does busybox. However, the busybox one threw a fit over the circular dependencies. The 'tsort' in 'coreutils' gracefully handles the circular deps, using perhaps random choice which one to install first.
I have written two scripts. Firstly, 'findwoofinstalledpkgs', which generates 'woof-installed-packages' and 'devx-only-installed-packages':
Then wrote 'sort-dep-order', which applies the topological sort and generates 'woof-installed-packges-dep-order':
woofV development is moving at a glacial pace, as it is a
complete rewrite relative to previous Woofs.
Tags: easy
hwclock fail in easyVoid 6.0.3
easyVoid 6.0.2 was released a little while ago, and the guys have been testing it. Some fixes have gone into 6.0.3, and it is built with the latest packages from the Void repo. There is a new problem:
# hwclock --hctosys --localtime
hwclock: settimeofday() failed: Invalid argument
#
# busybox hwclock --hctosys --localtime
hwclock: settimeofday: Invalid argument
#
# hwclock --hctosys
hwclock: settimeofday() failed: Invalid argument
This worked in 6.0.2! The function settimeofday() caused trouble back in 2020. I think it was glibc 2.31 that changed how that function worked, and there were reports of hwclock in the util-linux package and the busybox applet, both failing. They were fixed, and all was well -- until today.
6.0.2 has glibc 2.38_3 and 6.0.3 has glibc 2.38_5. That last digit is the revision-number. So it seems the Void developers have made a configuration change (or a patch) with the "_5" compile, that has introduced this problem.
So, what to do? I have a solution, though hated to have to do this. I booted up EasyOS Pyro-series version 1.3, which was released in December 2020. The Pyro-series started much earlier than that, and the packages were compiled in OpenEmbedded, with glibc 2.25 and util-linux 2.29.1, and function settimeofday() works "properly" -- that is, as it was originally designed, before glibc reduced its functionality.
I still have the OE Pyro build environment on one of my drives, and I created a recipe named 'hwclock-static_2.29.2.bb', that compiles just the hwclock utility in util-linux, linked with musl instead of glibc. And I get 'hwclock' utility statically-linked and weighing in at 118KB.
Which is very interesting, as the normal dynamically-linked (with
glibc) 'hwclock' utility in EasyOS Kirkstone, that I am running
right now, is 79KB. The statically-linked utility is not much
bigger.
What I will do is replace the 'hwclock' utility in util-linux, with the statically-linked one, in the next release of easyVoid. I know this is a cop-out; ideally should find out why this problem has occurred. But really, it is an annoyance that I just want to fix quickly.
EDIT:
The cause of hwclock fail was not due to glibc!!! I discovered
that the USB Flash drive is failing, causing various weird
effects.
Tags: easy
EasyOS Kirkstone-series version 5.7 released
It has been 7 months since the last announcement on Distrowatch; that was version 5.4. A huge amount of "water under the bridge" since then, and we are now at version 5.7. Certainly, overdue for another Distrowatch announcement.
The release notes from 5.4 to 5.7 can be found here:
https://distro.ibiblio.org/easyos/amd64/releases/kirkstone/2024/5.7/release-notes.htm
Picking through those, some highlights can be listed here. First, however, a general announcement blurb:
EasyOS is an experimental Linux distribution, that explores several concepts that are unique. EasyOS is standalone, that is, not based on any other distribution, and the Kirkstone-series is built with packages compiled from source in a fork of OpenEmbedded/Yocto. There is a page that itemizes how and why Easy is different from other distributions, here, but very briefly; container-friendly, runs fast in RAM, drive isolation, each app may be set to run as its own user, distributed as a drive-image file only (no ISO), frugal install, snapshot and rollback/forward, four packages managers, pup_event service manager, JWM-ROX desktop, folder encryption, hardware profiling. Also, not unique, but important; support for old computers.
EasyOS since version 5.4 was announced on Distrowatch, has undergone a myriad of changes; lots of little fixes and improvements, new applications and architectural features. Here are some highlights, in no particular order:
- New applications KeePassXC, Symphytum, Flowblade, p7zip
- More translations, in particular Turkish and Russian
- Improved support for VMs, with AQEMU and QtEmu
- Sudo replaced with "sudo-sh"
- Login and Security Manager overhauled
- Change folder hierachy to usr-merge, including /usr/sbin
- PKGget support to install Void .xbps packages
- Many system-level fixes, including network and samba
- Many app versions bumped, including Chromium, Htop, Limine, Global-IP-TV-Panel
- NVIDIA driver SFSs
- Install latest Chrome, Vivaldi and Firefox in menu
- Kernel now 5.15.148
- Sync'ed with OpenEmbedded/Yocto release 4.0.14
...this has only picked out a few highlights; please read the release notes for a more complete list, with links to blog posts. You might also find it interesting to read the announcement for version 5.4, for comparison:
https://bkhome.org/news/202306/easyos-kirkstone-series-version-54-released.html
Newcomers, download the drive-image file from here, courtesy of ibiblio:
https://distro.ibiblio.org/easyos/amd64/releases/kirkstone/2024/5.7/
A fast mirror in Europe, courtesy of NLUUG:
https://ftp.nluug.nl/os/Linux/distr/easyos/amd64/releases/kirkstone/2024/
Those already running EasyOS only need to click on the "update" icon on the desktop to update to 5.7.
If all that you know is ISOs and don't know how to write a drive-image file to a USB flash drive, read this:
https://easyos.org/install/how-to-write-easyos-to-a-flash-drive.html
You can also open up the drive-image file and install directly to
an internal drive. There are various tutorials about this at easyos.org.
Install in what we call "frugal mode" is extemely easy, especially
if you already have a boot manager installed, such as GRUB,
ReFInd, or Limine.
Feedback is welcome at the Puppy Linux Forum, in the EasyOS section:
https://forum.puppylinux.com/viewforum.php?f=63
If you browse recent posts on my blog, and in the forum, you will see a lot about a "next generation" EasyOS, that is for now codenamed "easyVoid", with a new build system named "woofV". Easy is already experimental; woofV is going to to be "experimental on steroids". It is slow going though, and cannot say when there will be an actual release.
Another parallel strain likely to emerge in 2024 will be the "Scarthgap-series", that will, maybe, supercede the Kirkstone-series. Just mentioning these projects; cannot say definitely yet what will finally materialise.
Note that despite these new projects, it is planned to keep the
Kirkstone-series going, as OpenEmbedded/Yocto will be supporting
it for the next couple of years. It is hoped that there will be a
seamless update from Kirkstone to Scarthgap via the desktop
"update" button.
Tags: easy
woofV installing packages into the rootfs
Continuing developing woofV, which is a complete rewrite of "Woof". Previous post, describing splitting packages into exe|dev|doc components:
https://bkhome.org/news/202402/woofv-splitting-packages-into-exe-dev-doc.html
I am gradually writing the scripts that will build the complete rootfs, ready to be converted to 'easy.sfs'. These scripts get executed, in order -- '1dl-start-pkgs', '2create-start-rootfs' and '3populate-rootfs':
https://github.com/bkauler/woofq/tree/main/easyos/easy-code/rootfs-skeleton/usr/local/woofV/rootfs
The heavy-lifter is the last one, '3populate-rootfs'. What it does is install all of the packages into folder 'rootfs', which includes PET, Kirkstone and Void packages -- and all done by the XBPS package management system.
'3populate-rootfs' calls 'template-fix', 'symlinks-fix' and 'pkg-split' in folder 'pkg-fix':
https://github.com/bkauler/woofq/tree/main/easyos/easy-code/rootfs-skeleton/usr/local/woofV/pkg-fix
'3populate-rootfs' also calls 'findwoofinstalledpkgs', 'sort-dep-order' and 'pet2xbps' in folder 'support':
https://github.com/bkauler/woofq/tree/main/easyos/easy-code/rootfs-skeleton/usr/local/woofV/support
Only bits and pieces of these scripts have been tested. I intend
to just keep coding; write the whole thing, then test
it.
Tags: easy
woofV splitting packages into exe dev doc
Woof, from the very early days, has script '2createpackages', that opens up each package, applying packages-templates if required, and generally getting it ready to copy into the rootfs. That last step is done by script '3builddistro'.
Another thing that '2createpackages' does is split the package up into "exe", "dev", "doc" and "nls" folders. The "dev" folders are what go into creating the devx SFS.
The splitting code is the same in WoofQ as in the early Woof v1; very slow and cumbersome. Woof-CE testing-branch has improved the script considerably:
https://github.com/puppylinux-woof-CE/woof-CE/blob/testing/woof-code/2createpackages
With woofV, it has turned out that I am rewriting Woof from scratch, including how the package splitting is implemented. I have written this script that does the actual splitting:
Void .xbps packages are already split; the development packages have "-devel" appended to their name. However, kirkstone package have everything in the one package, and need to have the development files taken out -- that is primarily what the 'pkg-split' script is for.
Taking documentation files out of .xbps packages is a problem. I don't want to have to open up everyone then rebuild it; a big hassle and would slow down building the rootfs considerably. So I'm going to cheat, and just delete the documentation files in the rootfs, before it gets made into 'easy.sfs'.
It does mean that each package information file in the XBPS
database, is going to be missing some files. I am hoping that does
not upset XBPS management.
Tags: easy
