hostname utility missing from Void repository
Thanks to the guys testing EasyShare in easyVoid, they are discovering problems. Caramel has reported that the 'hostname' utility does not work. easyVoid has the busybox 'hostname' applet, that is missing the required "-I" commandline option.
Caramel discovered that the Void package repository has packages
'net-tools-hostname' and 'inetutils-hostname' have variants of
hostname utility:
https://forum.puppylinux.com/viewtopic.php?p=110481#p110481
...neither of which have the "-I" option.
I checked the Debian package repo, at packages.debian.org, and they have package 'hostname', which has utility 'hostname'; this is the same package as used in EasyOS Kirkstone. And it supports the all-important "-I".
So, for the next release of easyVoid, it will have the 'hostname'
package from the Kirkstone repository.
Tags: easy
EasyOS Kirkstone-series version 5.6.7 released
Just after releasing 5.6.7, forum member Caramel reported that the 'sudo-sh' utility does not work:
https://forum.puppylinux.com/viewtopic.php?p=110652#p110652
It was fixed, sudo-sh version 1.3; however, Easy 5.6.6 got built with the old version, sudo-sh 1.2. So Easy 5.6.7 has just this one change.
See also the 5.6.6 release announcement:
https://bkhome.org/news/202401/easyos-kirkstone-series-version-566-released.html
Download:
https://distro.ibiblio.org/easyos/amd64/releases/kirkstone/2024/5.6.7/
Hopefully no more showstoppers!
Tags: easy
Package name translation OE to Void
easyVoid is built with many packages from EasyOS Kirkstone-series. These are packages compiled in OpenEmbedded. woofV will build easyVoid from Void .xbps, Kirkstone .tar.xz and .pet packages. The build process converts the .tar.xz and .pet packages to .xbps and then installed with the XBPS package manager. At least, that's the plan.
One important step to avoid confusing XBPS is that the .tar.xz-converted packages should have the same name as one that might already be in the Void package repository. For example, OE names all packages lower-case, such as 'libxau', whereas Void names it 'libXau'. Another example is hyphen inserted, for example 'psc-lite' and 'psclite'.
Note that mostly Kirkstone packages are used when the same does
not exist in the Void repository, such as 'rox-filer', so naming
is not an issue. In a few cases though, such as 'networkmanager',
have chosen the Kirkstone package instead of the Void
'NetworkManager'.
I wrote a script that finds these equivalent packages but with different names, and have uploaded translation tables here:
Slowly but surely working toward woofV becoming functional. As long as no show-stopper comes along.
Tags: easy
woofV packages-templates redesigned
Continuing the woofV project. Recent relevant blog posts:
- Tweak Kirkstone package db format — January 28, 2024
- Installing PET packages in XBPS-managed system — January 24, 2024
- woofV create initrd — January 23, 2024
- Start create woofV builtin to EasyOS — January 22, 2024
Woof, right from the very early days, has a folder 'packages-templates', which, in a nutshell, has hacks to modify a package before and after installation. Back in the early days, the main reason for this mechanism was to reduce the size of packages. Another purpose was that packages could come from different distribution repositories, and might need some massaging -- for example some files kept in unexpected places.
We are not so much concerned about size reduction these days; however, 'packages-templates' is still useful. The format of information in 'packages-templates' has remained the same in WoofQ as the very early Woofs. Same as Woof-CE "legacy" branch:
https://github.com/puppylinux-woof-CE/woof-CE/tree/legacy/woof-code/packages-templates
This old mechanism is extremely cumbersome and slow to process. The Woof-CE developers have, over the years, simplified it. In particular, forum member dimkr has worked on it, see the "testing" branch:
https://github.com/puppylinux-woof-CE/woof-CE/tree/testing/woof-code/packages-templates
The very ambitious plan for easyVoid is to have a new Woof, "woofV", and it will be builtin, available in a running easyVoid. It will be found at /usr/local/woofV. In /usr/local/woofV/pkg-fix is the folder 'packages-templates'.
The time has come for me also to redesign the format in 'packages-templates'. Here it is:
It took a couple of very intense and tedious days to convert the old format to the new one. Anyway, just now finished and uploaded.
The script that reads the information in 'packages-templates' has not been uploaded, as it is still in a state of flux. What will happen is that each package that has a matching folder name under 'packages-templates', is expanded, processed, then rebuilt into a package and then installed with the XBPS package manager into the rootfs.
easyVoid is also built with a lot of Kirkstone packages, and they
will be processed the same way. Whether requiring processing via
'packages-templates' or not, they will always be opened up and
rebuilt as .xbps packages, so that the XBPS package manager can
install them.
Tags: easy
EasyOS Kirkstone-series version 5.6.6 released
Online release notes:
https://distro.ibiblio.org/easyos/amd64/releases/kirkstone/2024/5.6.6/release-notes.htm
Here are the highlights, since 5.6.5:
- Tweak Kirkstone package db format — January 28, 2024
- MSCW not run at first bootup — January 27, 2024
- mdview update compiled in OpenEmbedded — January 27, 2024
- mdview markdown viewer updated — January 27, 2024
- Fix sudo-sh segfault — December 19, 2023
- sudo-sh Cancel button — December 18, 2023
- Improved Firefox user-settings and default browser — December 17, 2023
- Download Chrome browser in menu — December 15, 2023
- Yocto 4.0.14 release recompile — December 15, 2023
- Fix some .desktop files getting deleted — December 14, 2023
- Fix Firefox second instance will not start — December 13, 2023
Download the drive-image file:
https://distro.ibiblio.org/easyos/amd64/releases/kirkstone/2024/5.6.6/
Feedback is welcome in the EasyOS section of the Puppy Forum:
https://forum.puppylinux.com/viewtopic.php?p=110536#p110536
Have fun!
Tags: easy
Tweak Kirkstone package db format
The "Puppy package database" format goes right back to the early days of Puppy, and still used in EasyOS. This is what 'petget' and 'PKGget' (PPM) understand. For a pup built with, say, Debian .deb packages, the Debian package database is converted to Puppy-db format.
The pup-db format is very simple; each package db entry is on one line. In the case of EasyOS Kirkstone-series, the binary packages are imported from OpenEmbedded and file 'Packages-oe-kirkstone-official' create, which is the pup-db format. You can find this file in /root/.packages. Here is one line of that file:
acl-2.3.1-r6|acl|2.3.1|r6|BuildingBlock|628K|kirkstone|acl-2.3.1-r6-nocona-64.tar.xz|+attr|Utilities for managing POSIX Access Control Lists|oe|kirkstone||
The tweak that I have made, is that it used to be (up until EasyOS 5.6.5):
acl-2.3.1-r6|acl|2.3.1-r6||BuildingBlock|628K|kirkstone|acl-2.3.1-r6-nocona-64.tar.xz|+attr|Utilities for managing POSIX Access Control Lists|oe|kirkstone||
...that fourth field is supposed to contain the package revision-number, or build-number. However, I hadn't separated the "-r6" from the third field, the version number.
It is a small change, just making it more as originally intended.
Hopefully this fix won't upset any scripts.
Tags: easy
MSCW not run at first bootup
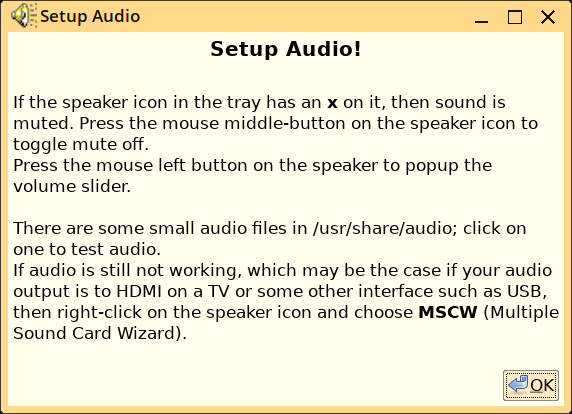
In a pristine new install of EasyOS, at first bootup the MSCW
(Multiple Sound Card Wizard) runs.
MSCW is supposed to enable you to select between different audio interfaces, unmute and set the level; however, some people have reported that it messes up the sound, that is, sound does not work until after a lot of messing around.
Those people have found it best to not run MSCW at all; instead, just middle-click on the speaker icon, then left-click to bring up the volume.
I need to study the MSCW code and try and figure out why it isn't working properly for some people. In the meantime, a quick fix is to not run MSCW automatically at first bootup; instead, run this:
Note, EasyOS Kirkstone-series version 5.6.6 is expected to be
uploaded very soon.
Tags: easy
mdview update compiled in OpenEmbedded
Continuing from the post earlier today:
https://bkhome.org/news/202401/mdview-markdown-viewer-updated.html
mdview version 2023.12.12 has been compiled in OpenEmbedded and
will appear in the next release of EasyOS, Kirkstone-series. That
will be 5.6.6 and probably will be uploaded in a few
days.
Tags: easy
