mdview markdown viewer updated
Forum member jamesbond is the developer of mdview. Here is his original documentation in 2015:
https://www.lightofdawn.org/blog/?viewDetailed=00141
Forum member don570 informed me that EasyOS has a very old version. Yes, James has been updating it, and the latest is using gtk3. I downloaded the 2023.12.12 source tarball, with the intention of compiling it in OpenEmbedded.
I upload source packages to ibiblio.org ...except that ssh login is currently not working. Not just me, others cannot login either:
We are so reliant on all of these services to work! Just today I was watching a documentary how reliant we are on undersea fibre-optic cables; we would be paralyzed if a hostile entity cut them.
To compile the source in OE, need to give a URL for the source. Well, could get it direct from Jame's Fossil repository. Anyway, have uploaded the source tarball to this blog:
Very interesting the other old projects that James is maintaining:
https://chiselapp.com/user/jamesbond/
Tags: easy
Installing PET packages in XBPS-managed system
Continuing with developing woofV, here is the previous post:
https://bkhome.org/news/202401/woofv-create-initrd.html
woofV will build easyVoid built with .xbps packages -- nothing new yet, that is what easyVoid 6.0.1 does -- but woofV will build using the XBPS package management system.
There is a vital distinction here. 6.0.1 is like the traditional pups; binary packages of any distro can be used (what we call the "compatible" distro). The method is that the package database of that distro is converted to "Puppy DB" format, and PKGget (or PPM in the case of the pups) is used as the package manager. The package manager of the original distro, such as APT for Debian, or XBPS for Void, is not used at all.
If you have used easyVoid 6.0.1, you will have seen that PKGget
works OK. It is a nice GUI for installing packages. It also has a
great advantage, compared with most other package managers, in
that it is a chameleon -- it can install just about any type of
package, for example .deb, .rpm, .tar.xz, .pet or .xbps.
Some of the recent pups and derivatives have given up on the PPM
and adopted the package manager of the compatible distro. The
basic reason is, it is very difficult to have both.
With woofV I am attempting to build easyVoid based on XBPS package manager, retaining PKGget as a GUI frontend. Which is quite a challenge.
As a step in this direction, I have written a script that installs .pet packages and also registers them with XBPS. There are two main hurdles:
- Most .pet packages are not usr-merge
- The XBPS manager cannot install a .pet package, only .xbps
All of the Woofs have a table, a variable PKGS_SPECS_TABLE, with a list of packages that are to used to build the SFS (or multiple SFSs) which will be the rootfs. These packages can come from different places, some from the compatible-distro, some from other distros, and some PETs.
If the core package manager is XBPS, then a PET package will have to be converted. Firstly, converted so that the folder hierarchy is usr-merge. Secondly, converted to a .xbps package so that XBPS manager can install it.
That is what this script, 3populate-rootfs, does:
...cannot guarantee that what you see there right now is working; it was, but I have made some enhancements before uploading to github and not yet tested. The script shows the principles anyway.
There were issues with a few PETs; the 'xbps-create' script couldn't convert to .xbps. For example:
Success, folder tas-1.15-easyos created
xbps-create: ERROR: invalid pkgver! got `tas-1.15-easyos_1' expected `foo-1.0_1' No such file or directory
ERROR: NAME='tas' VER='1.15-easyos_1'
ERROR failed: xbps-create -n "tas-1.15-easyos_1" -s "Screenshot utility" -A x86_64 -D "" "/mnt/wkg/data/woofV/sandbox/tas-1.15-easyos"
...those last two "ERROR: ..." lines are echo statements that I put into the script to try and figure out what is going wrong.
The PET is 'tas-1.15-easyos.pet' and expanded to folder 'tas-1.15-easyos'. I do not know why xbps-create objected to the name-version string of "tas-1.15-easyos_1". There were so many other PETs with far weirder package naming that xbps-create was quite happy with. Really odd.
I will play with renaming the PET, maybe to 'tas-1.15.pet',
surely that will be acceptable. Hopefully "tas" is not some kind
of keyword.
Tags: easy
woofV create initrd
The previous post introduces "woofV", which is the Woof build system, in this case for building from Void packages and builtin to easyVoid. Previous post:
https://bkhome.org/news/202401/start-create-woofv-builtin-to-easyos.html
There are some major challenges ahead, but one step at a time. I have implemented a script, 'create-initrd', that does what the name suggests. See commit:
https://github.com/bkauler/woofq/tree/main/easyos/easy-code/rootfs-skeleton/usr/local/woofV/initrd
Any user of easyVoid can run the script and create a new updated
'initrd' file, at /mnt/wkg/data/woofV/initrd/. There is a bit more
that has to go into it, but it is basically
working.
Tags: easy
Start create woofV builtin to EasyOS
There are many Woofs, from the original "Puppy Unleashed", to Woof v1, then Woof2, then Woof-CE and WoofQ. Plus some other variants. In a nutshell, what they do is put together binary packages from a Linux distribution and create .sfs files, an intrd and vmlinuz, and put it into a drive-image or ISO file.
WoofQ started life in 2013 as a successor to Woof2, at the same time as Woof-CE. WoofQ was originally used to build Quirky Linux, then later, in 2017, EasyOS.
Now that easyVoid is underway, with rolling-release model, it is
time for a complete rethink.
One of the rethinks is that Woof can be builtin to easyVoid, not as a separate project on github. The "update" icon on the desktop will be repurposed to run woofV and build new 'easy.sfs', 'vmlinuz' and 'initrd' and then perform a version update. All done by the user.
WoofV is a very ambitious project; anyhow, I have made a start. Have written a script that creates the skeleton drive-image file that will become 'easy-<version>-<architecture>.img'. This has two partitions, by default a 7MiB esp and a 880MiB ext4. Script is here:
Next up, looking into creating a very basic rootfs using xbps
package management.
Tags: easy
easyVoid version 6.0.1 released
See 6.0 blog announcement:
https://bkhome.org/news/202401/easyvoid-version-60-released.html
Still to be considered as alpha-quality.
See the forum for photo, download link and ongoing discussion:
https://forum.puppylinux.com/viewtopic.php?p=109563#p109563
Tags: easy
easyVoid version 6.0 released
This is the very first release of easyVoid; EasyOS built from Void Linux binary packages. Despite the "6.0", this is an alpha-quality release and is intended for testers. Here are earlier blog posts:
- Thinking how to manage the Void rolling release model — January 19, 2024
- easyVoid is looking good — January 18, 2024
- The return of EasyVoid — January 12, 2024
Download the drive-image file from here:
https://distro.ibiblio.org/easyos/amd64/releases/void/
Newcomers to EasyOS are recommended to write the image-file to a USB-stick and boot from that. If you need guidance how to do that, read here:
https://easyos.org/install/how-to-write-easyos-to-a-flash-drive.html
...please use a USB drive of at least 16GB. It is also possible to do a direct install to internal drive; see tutorials at easyos.org.
easyVoid is being discussed on the Puppy Forum here:
https://forum.puppylinux.com/viewtopic.php?t=9553
There are some profound enhancements being dreamed of for the future of easyVoid; this will be on top of what is already an experimental distribution. It depends on no showstoppers being discovered, and my continued enthusiasm for this new direction, but may become an exciting new journey.
Anyway, although enhancements are planned, the fundamental
operations of installing and running apps, setting up and using
system utilities such as samba and bluetooth, should remain the
same, and testers are welcome to try these. Report success/failure
to the forum, and even better if you fix something let us know.
Tags: easy
Thinking how to manage the Void rolling release model
I posted yesterday about liking how easyVoid has turned out:
https://bkhome.org/news/202401/easyvoid-is-looking-good.html
...Flapi, the Flatpak manager, is now working, and various other issues fixed, so now looking even better.
Version 6.0 will probably be released this weekend, but I have been thinking of strategies to play nicely with the Void rolling-release model. If you were to install Void itself, then there are no future release numbers; you just keep syncing with the latest packages. EasyVoid could do the same thing.
The "update" icon on the desktop could work in a new way. Clicking on it, could download the latest packages from the Void repository, and build new 'easy.sfs' and 'devx.sfs' files. There would then be a version-update based on these files.
What this would mean is that easyVoid users can update on their
own. They will not have to wait for me to release a new version of
easyVoid. Although I will be releasing version 6.0, after that the
version numbers will be by date, in format year-month-day, for
example 240318.
EasyVoid would work like EasyOS, /mnt/wkg/releases has a history
of past versions, or in this case, dates. If you were to update
from, say, 240228 to 240318, but find that things have gone bad --
which is always a risk with the rolling-release model, no problem,
just reboot and choose to roll back to the previous version.
I won't have to be constantly working to release new versions. I could go off into the Outback on my trike, or even "fall off the perch" as my step-grandad used to say, and easyVoid users can just keep on updating.
The "update" icon can also be made to read a patch-file from somewhere, if any fixes to the 'initrd' or 'easy.sfs' are required. Then there is the requirement to update the kernel -- and currently easyVoid requires a different kernel from the official Void ones.
The devil is in the details of course. The most likely way to implement this is to have a "mini Woof" builtin to easyVoid, let's say at /usr/local/woofv -- yeah, call it "woofV".
The kernel, yeah, a problem. It uses aufs, whereas Void kernel only has overlayfs. EasyOS relies on a big kernel, with all drivers builtin to access drives and HID devices. My very limited exposure to Dracut, as used for the Void kernel, is not good. Possibly woofV could also compile the latest kernel, or we could have a repo where a small band of easyVoid users can upload stuff, such as kernels.
Anyway, this is all very interesting. easyVoid 6.0 will be
released, and it will have to be considered as an "alpha" release,
because of my very limited testing. Testers will be most welcome!
I will apply fixes, and hopefully implement "woofV" and at some
time not to far in the distance, release easyVoid stable, not as
6.1 but as a date, like 240228.
Tags: easy
easyVoid is looking good
The previous blog post is about returning to easyVoid:
https://bkhome.org/news/202401/the-return-of-easyvoid.html
We have been discussing easyVoid on the forum:
https://forum.puppylinux.com/viewtopic.php?t=9553
As I am working on it, it continues to be a pleasant experience. There are issues, that I will work on; however, reckon will go for it and release easyVoid version 6.0 soon.
Decided to jump to version "6" as this might be the start of something quite different. Testers will be welcome, and there are bound to be bugs, so the first stable release will probably be 6.1.
Not that we can really achieve a "stable release" with the Void rolling-release model. That is something that I have ideas to improve. Whether those ideas come to fruition depends on whether still happy with easyVoid after a few more weeks of development.
6.0 will not have the xbps package manager, relying totally on
PKGget.
I tested on my old Compaq Presario, with Intel Core2 CPU and 2GB RAM -- easyVoid runs great. Didn't do much, just ran Firefox and watched a 720p YouTube video.
On my Lenovo desktop PC, with i3 CPU and 32GB RAM, at first bootup there was some video wierdness. Mostly text was rendering with characters missing. Xorg had chosen the 'intel' driver, which rang a bell; exited from X to the console, ran "xorgwizard" and it told me that the intel driver is using "sna" acceleration and offered to change to "uxa". Which I accepted, and video now OK.
Anyway, here is a photo, taken on the Compaq:
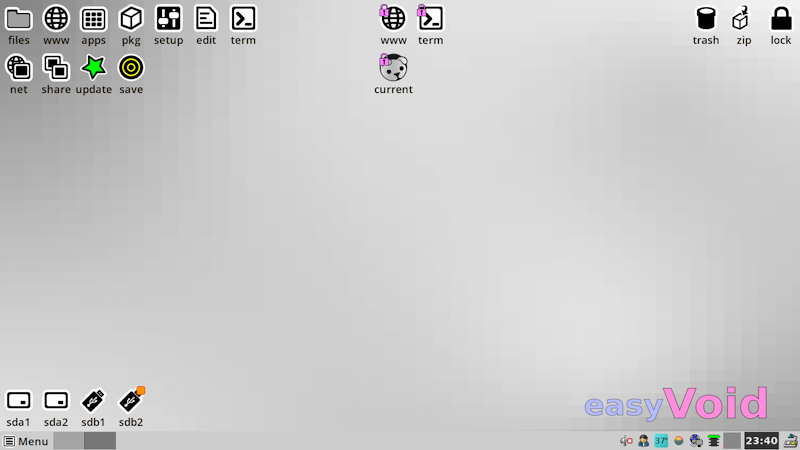
...yeah, decided to put together a new theme. Rather bland grey seems appropriate for a "void" distro. It looks alright I think. I have never been satisfied with grey themes, but this one seems passable.
As usual, have included lots of apps builtin. Firefox browser instead of Chromium, as FF is running fine, no flickering. This is the very latest FF. LibreOffice, Inkscape, heaps more included.
Tested printing, audio, working.
So what doesn't work? Flapi fails. Haven't tried Samba. I will
see if can fix Flapi before releasing 6.0. Other things, like
Samba, testers will be welcome.
Tags: easy
