QV lockdown implemented
About a week ago, I posted about the return of Quirky Linux:
https://bkhome.org/news/202403/quirky-has-returned.html
...well, not exactly; this is a somewhat different beast. I have named it "Quirky Void", or just "QV". Which may also be the Latin words "Quantum Vīs", meaning "as much as you want".
Those using EasyOS will know about Lockdown modes. The most stringent is bootup and run in RAM, with all drives disabled. Lockdown is described here:
https://easyos.org/user/ultra-secure-web-browsing.html
QV does not use a layered filesystem, nor Squashfs files; it is a traditional installation. With a significant difference that QV can install into a folder in a partition. In Puppyland, we refer to that as a "Frugal installation".
The ability of QV to install into a folder inside a partition is important; it is possible to lock the user inside that folder, unable to see outside. Hence Lockdown can be achieved.
Like EasyOS, QV has a little menu in the initrd. Here is the QV menu:
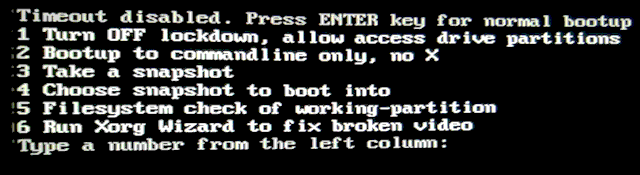
...notice item-1. Previously, item-1 had "Turn ON lockdown, disable access drive partitions", which I chose. By choosing item-1 again, I can toggle Lockdown off.
Oh, one thing. The menu had a message "Hit the SPACEBAR to
disable 15-second timeout", because it will timeout then bootup
will happen. But if you want more time to read the menu items,
just hit the SPACEBAR and you will get the menu as shown above.
So, it is currently in Lockdown-mode; I just press the ENTER key and after bootup:

...the important thing to see in that photo is only one partition icon is displayed. That is the working-partition. In fact, you can't even mount that and access outside the '@qv' folder. In the previous blog post, there is this image, showing the folder hierarchy in the USB-stick:
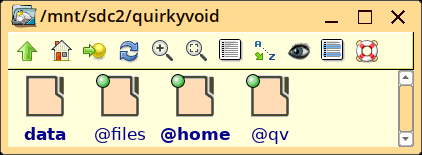
The 'init' script in the initrd has booted into the '@qv' folder. 'data', '@files' and '@home' are bind-mounted on '/data', '/files/ and 'home' inside '@qv', so they are accessable. But that's it, cannot access anything else in /mnt/sdc2, nor any other partitions.
You are still running as the root user, administrator, but it is "crippled root". Here is some of the code in the 'init' script in the initrd:
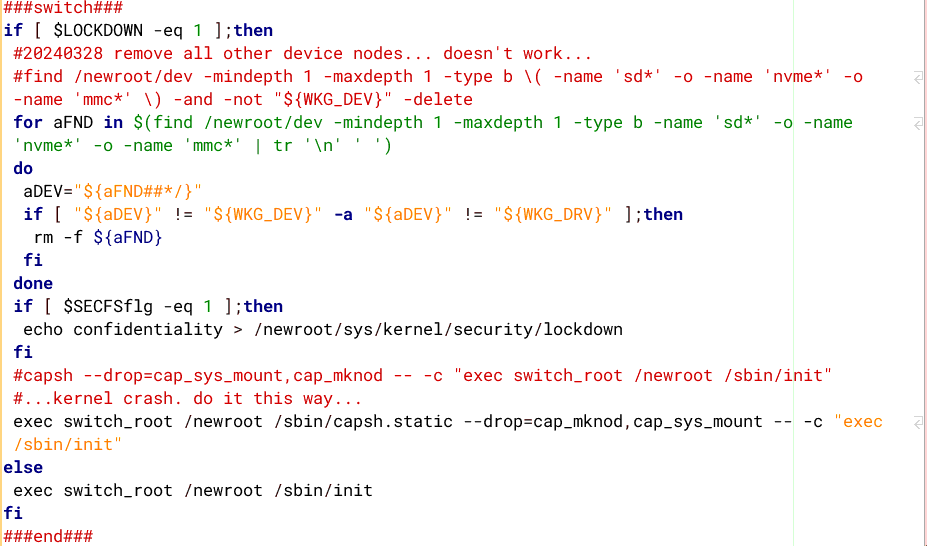
The ability to prevent mounting of partitions relies upon
dropping "cap_sys_mount". Linux Capabilities allows selective
dropping of the administrator's capabilities. Unfortunately, the
designers created "cap_sys_admin" which, when dropped, takes away
just about all of administrator's capabilities, making it hardly
more than a normal user -- cap_sys_admin also drops ability to
mount partitions. It really should have been broken into smaller
pieces.
So, I have a patch, that separates out the ability to mount from cap_sys_admin; named cap_sys_mount. I can then just drop ability to mount, while keeping all of the rest of cap_sys_admin capabilities. The patch for the 6.8.1 kernel can be found here:
https://distro.ibiblio.org/easyos/source/kernel/6.8.x/6.8.1-20240325/
That cap_sys_mount patch origin is described here:
https://bkhome.org/news/202012/kernel-510-lockdown-success.html
...I have modified the original patch a bit, and it also required a fix for the 6.8.1 kernel.
QV now has Lockdown, and I kept it very simple. There are no
types of Lockdown; just the one. EasyOS has the ability to plugin
a USB drive and can save to that; however, QV doesn't need that,
as it already saves direct to the working-partition. Plugging in a
USB drive won't work in QV; it cannot be mounted, even though the
partition icon(s) will appear.
Note also, like EasyOS, when in Lockdown mode, the 'init' script in the initrd will detect any HDD (rotating platter drive) and power it down. So it will be turned off, which is an extra security mechanism.
In Lockdown mode, swap partitions are also disabled. However, you can create a swap file in '/data', and that will be automatically used. Name it "pupswap.swp".
QV's Lockdown mode is pretty good. You can do everything that you would normally do, except not access any other partitions. You have all the space in the working-partition, so use a big enough partition for any foreseeable requirements. Probably if running off a USB-stick, at least 16GB would be OK, preferably 32GB.
However, there may be some applications that will want to perform
a mount operation. That will fail. Haven't tried Flatpaks yet. A
Flatpak app runs as a user (same name as the executable), but it
can bump its Linux Capabilites and acquire some root abilities.
The ability to do this is required by Flatpaks, and back then I
was very reluctant to enable that feature in the kernel. I forget
the particular kernel config that allows capability-jump. However,
in the case of QV, the ability to mount is removed while still in
the initrd, so it is gone and cannot be bumped up to by a Flatpak
app.
Tags: quirky
