Fix JWM not recognize custom keyboard layout
Forum member Caramel posted about the problem in the forum, with a fix:
https://forum.puppylinux.com/viewtopic.php?t=12241
I have put code into /root/.xinitrc:
https://github.com/bkauler/woofq/commit/e6c7a602edc1e89e04ebee165ded6e154b419ce7
Tags: easy
Dolphin removed from Flappi, KTorrent added
I posted this morning that KDE Dolphin has been added to Flapi:
- KDE Dolphin file manager added to Flapi — July 25, 2024
On the forum, we determined that the 'udisks2' package needs to be installed, via PKGget. However, there are still weird unresolved issues, see forum thread:
https://forum.puppylinux.com/viewtopic.php?p=126968#p126968
We already have file managers in EasyOS, with the possibility of adding more of them, as native apps. So I have removed Dolphin from Flapi.
Have added KTorrent BitTorrent client. See homepage:
https://apps.kde.org/ktorrent/
Github commits:
https://github.com/bkauler/woofq/commit/d58b3730bd1363563ec6c511ef7d68449fafcd1b
https://github.com/bkauler/woofq/commit/b0b31f756e3462e070ed99cf41946acb580a1a82
Tags: easy
KDE Dolphin file manager added to Flapi
Forum member Federico posted about unable to run KDE Okular and Dolphin in Easy 6.1.1:
https://forum.puppylinux.com/viewtopic.php?p=126953#p126953
See my replies. I advised to not install foreign packages. Okular is available via Flapi, the Flatpak installer. I have now added Dolphin permanently in Flapi, see github commits:
https://github.com/bkauler/woofq/commit/5af9060b81bdb4422245b12045c62fbb113505ca
https://github.com/bkauler/woofq/commit/6cc1b23c86ebcd5c376d59879ed0549c01d52609
Here is the Dolphin homepage:
Tags: easy
Fenders for custom trike
Continuing the custom tadpole recumbent trike project, here are recent posts:
- Foot and leg safety on a recumbent trike — July 10, 2024
- Bash plate for trike — July 09, 2024
- Wheel knuckle modifications — June 29, 2024
The trike came with mudguards (fenders in US English); however, I have to create brackets to mount them in this custom project. Yes, the Wikipedia states that "bicycle fender" is US English, whereas "mudguard" is British English.
As the front now has shock absorber suspension, had to create brackets to hold the fenders:

The rear of the trike came with a tray mounted on the swing-arm, with fender bolted underneath the tray. However, I want the tray, and panniers mounted beside it, to be on the suspended part of the trike frame, not on the swing-arm. It is a basic principle that as much weight as possible be above the shock absorber, not below. So, have to redesign tray and fender mounting.
The fender is still attached to the swing-arm. I used whatever scrap aluminium strap at hand and found mount points the strap could be bolted to:
 |
 |
...notice at bottom-left of first photo, there is a small
aluminium plate that I riveted to the swing-arm, to attach the
bottom-end of the fender.
There is progress, albiet slowly. Waiting on arrival of a short
length of aluminium tube, 55mm OD, that will slide into the trike
frame and to which the tray can be attached.
Tags: light
EasyOS Scarthgap-series version 6.1.1 released
Earlier releases; in particular read 6.0 announcement if new to EasyOS:
- EasyOS Scarthgap-series version 6.1 released — July 13, 2024
- EasyOS Scarthgap-series version 6.0.4 released — July 07, 2024
- EasyOS Scarthgap-series version 6.0.2 released — June 24, 2024
- EasyOS Scarthgap-series version 6.0 released — June 18, 2024
Release notes:
https://distro.ibiblio.org/easyos/amd64/releases/scarthgap/2024/6.1.1/release-notes.htm
Download:
https://distro.ibiblio.org/easyos/amd64/releases/scarthgap/2024/6.1.1/
Mirror in Europe courtesy of NLUUG:
https://ftp.nluug.nl/os/Linux/distr/easyos/amd64/releases/scarthgap/2024/6.1.1/
Feedback is welcome at the Puppy Forum:
https://forum.puppylinux.com/viewtopic.php?p=126786#p126786
Have fun!
Tags: easy
Xvkbd now in tray
EasyOS used to have Xvkbd, the virtual keyboard, in the system tray. It got taken out when the alternative icon-free-desktop mode was introduced, as the tray was getting very crowded. There is ongoing interest in the virtual keyboard, so I decided to put it back in the tray.
Compile of Xvkbd 4.1 was reported earlier today:
https://bkhome.org/news/202407/xvkbd-41-and-limine-7120-compiled-in-oe.html
I have built Easy 6.1.1, to be uploaded soon, and here is the desktop:
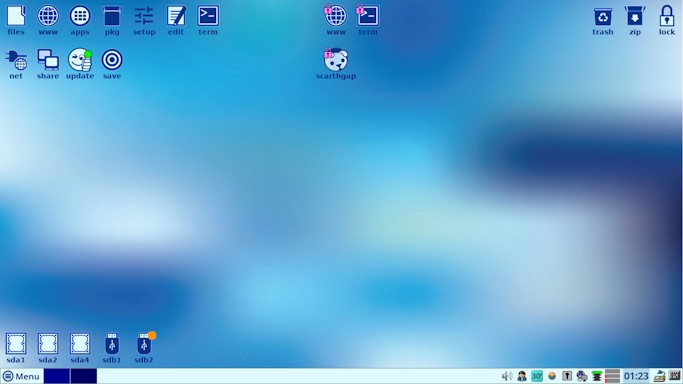
...look at the extreme bottom-right corner.
This snapshot is a new install; if update to 6.1.1, won't get Xvkbd in the tray, will have to run EasyJWM to choose it to be in the tray.
Here is the github commit showing how Xvkbd was chosen to be in the tray by default:
https://github.com/bkauler/woofq/commit/34dd19269ce89b91a70e73719c38453947883999
Decided to do a new wallpaper also.
Limine 7.12.0 is working for me, tested on my old Compaq Presario
with traditional BIOS, and the Lenovo Ideacentre with UEFI. Both
OK.
Tags: easy
Xvkbd 4.1 and Limine 7.12.0 compiled in OE
EasyOS has Xvkbd 3.8; however, latest is 4.1 which has improvements. Forum discussion here:
https://forum.puppylinux.com/viewtopic.php?t=12167
So, have compiled 4.1 in OpenEmbedded. The new recipe here:
https://github.com/bkauler/oe-qky-scarthgap/commit/e41a9c66079c6a7f270cfb813eb889bddd05cc0c
A couple of days ago, posted about Limine 7.12.0:
- ext4 support has returned in Limine bootloader — July 21, 2024
Limine 7.12.0 has been compiled in OE. Here is the recipe:
https://github.com/bkauler/oe-qky-scarthgap/commit/c2be5289300e8a482a23b680af3556857501d599
Tags: easy
Chinese language PETs
Forum member icake provides Chinese language support for the pups, including EasyOS Scarthgap-series:
https://forum.puppylinux.com/viewtopic.php?p=124710#p124710
I have put them into the "pet-scarthgap" PET repository, installable via PKGget. Have renamed them to, I think, be more meaningful:
chinese-stage1-fcitx-21.4.0.pet
chinese-stage1-gcin-21.4.0.pet
chinese-stage1-hime-21.4.0.pet
chinese-stage1-scim-21.4.0.pet
chinese-stage1-yong-21.4.0.pet
chinese-stage2-zhcn-21.4.0.pet
chinese-stage2-zhhk-21.4.0.pet
As icake has explained, one of the stage1 PETs need to be
installed, then one of stage2. I haven't uploaded them
yet.
Tags: easy
